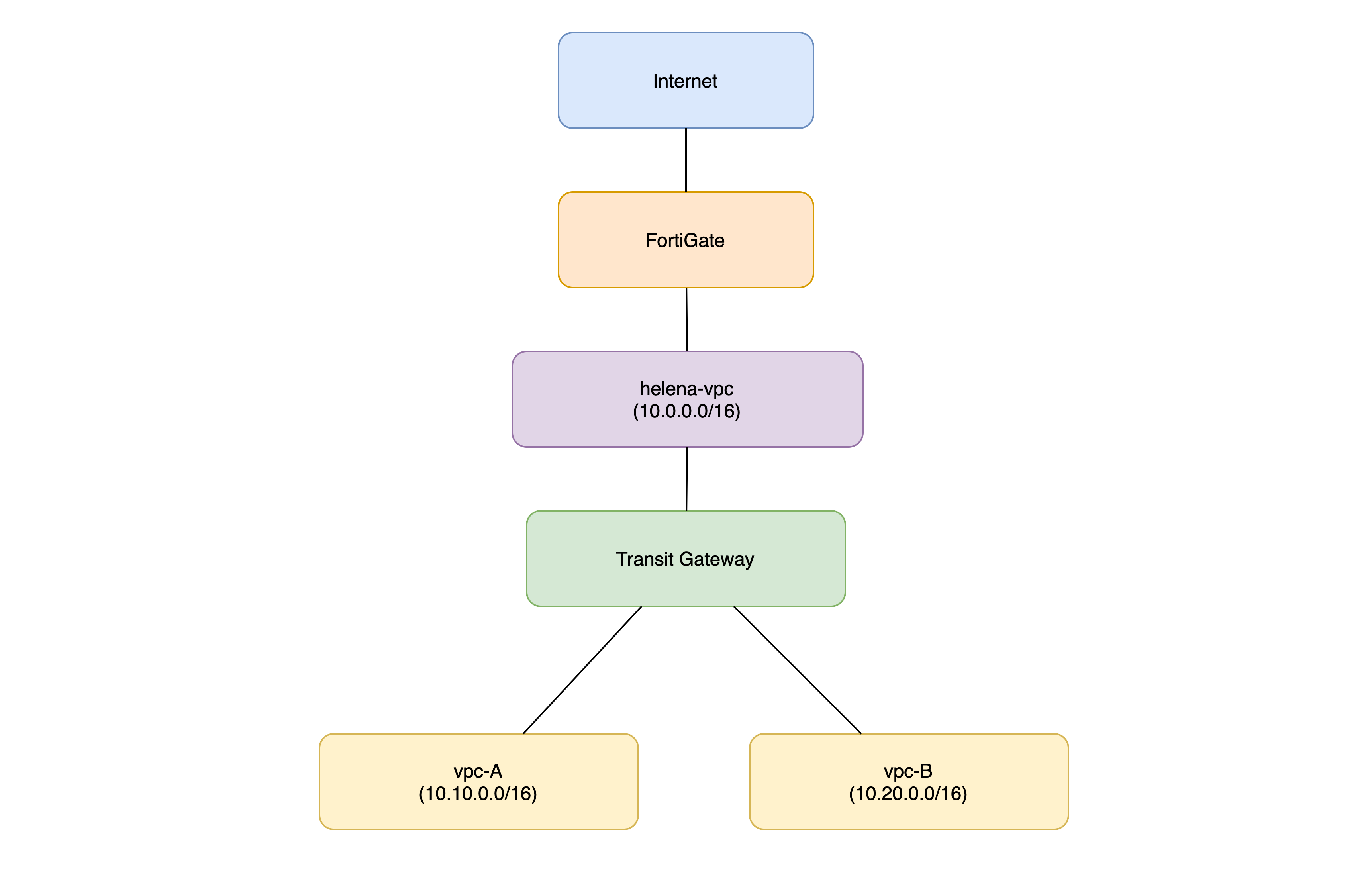
AWS Transit Gateway
AWS Transit Gateway is a centralized routing hub that connects multiple VPCs, VPNs, and on-prem networks through a single, scalable, highly available service. Instead of building many VPC-to-VPC peering links, you attach each network to the Transit Gateway and let it handle all routing between them.
Here we are continuing from this AWS with Fortigate Lab and we plan to add 2 more VPSc that we will interconnect using Transit Gateway
Configuring VPC
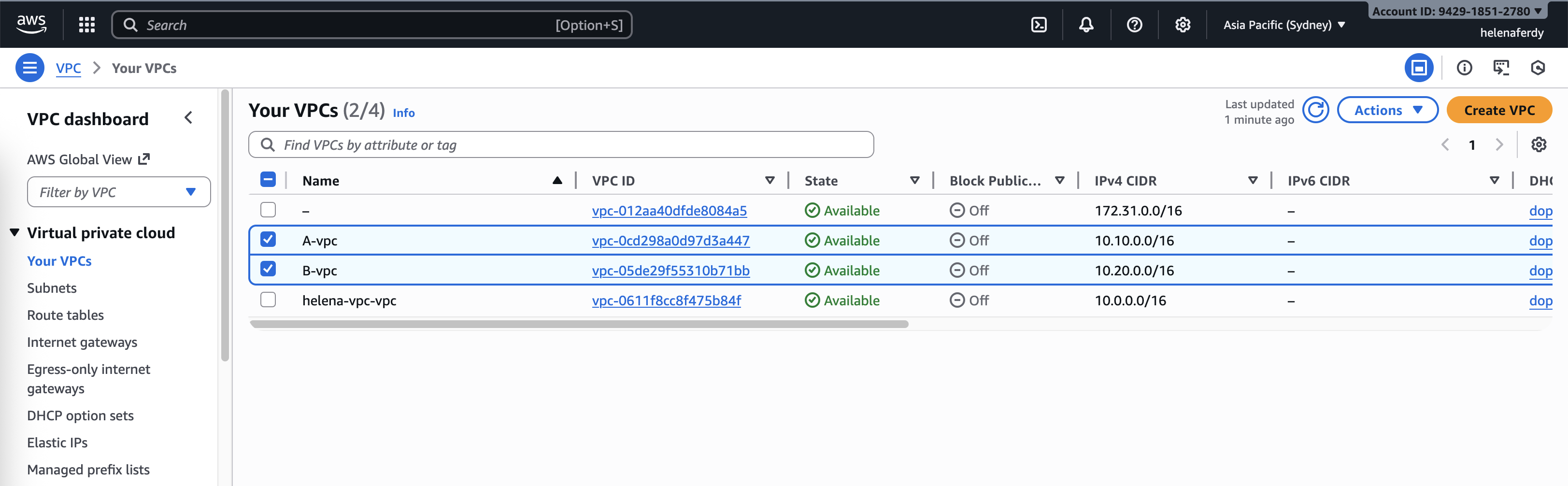
We add 2 more VPCs, A-VPC and B-VPC on top of already existing helena-VPC
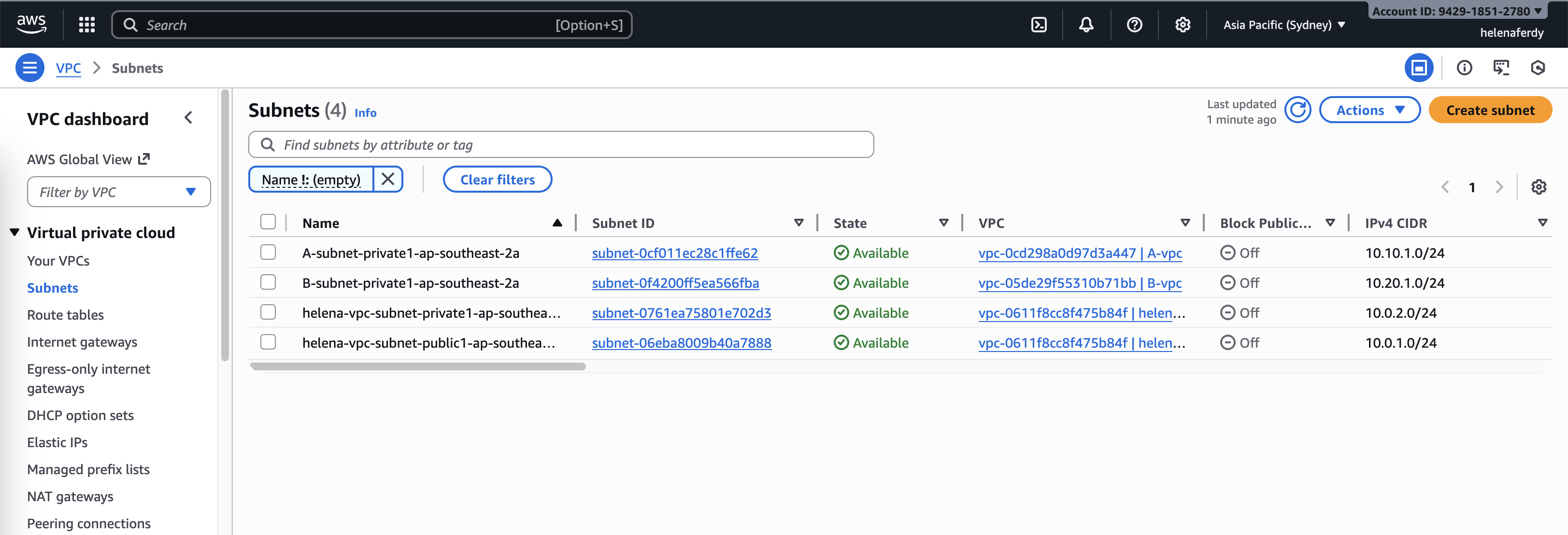
Then we add its respective subnets, where A & B VPC will only have private subnets with no direct internet connection
We make sure these new VPCs don’t have default gateway yet, we’ll configure it later
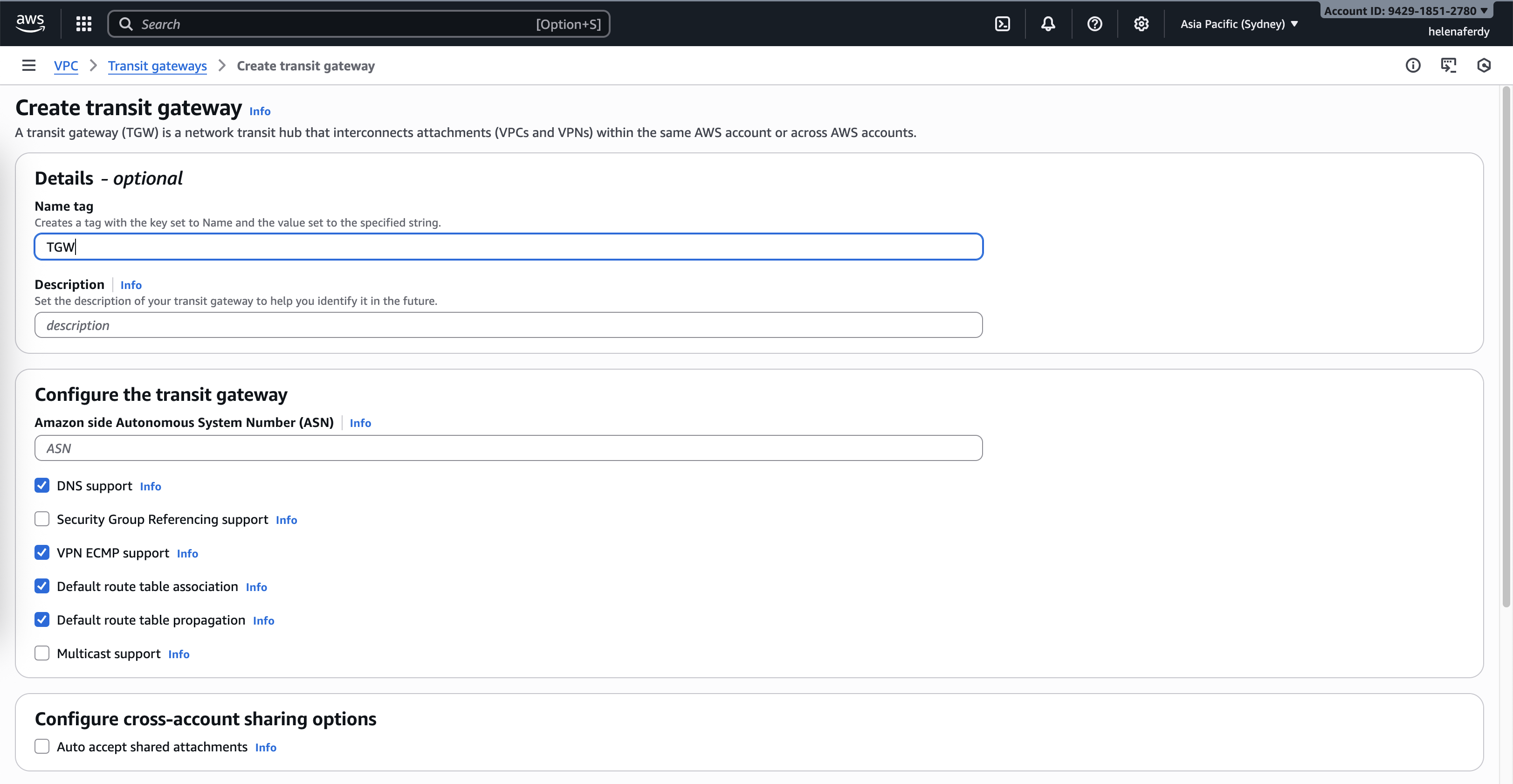
Configuring Transit Gateway
On VPC » Transit Gateways » Create Transit Gateway with all default values unchanged
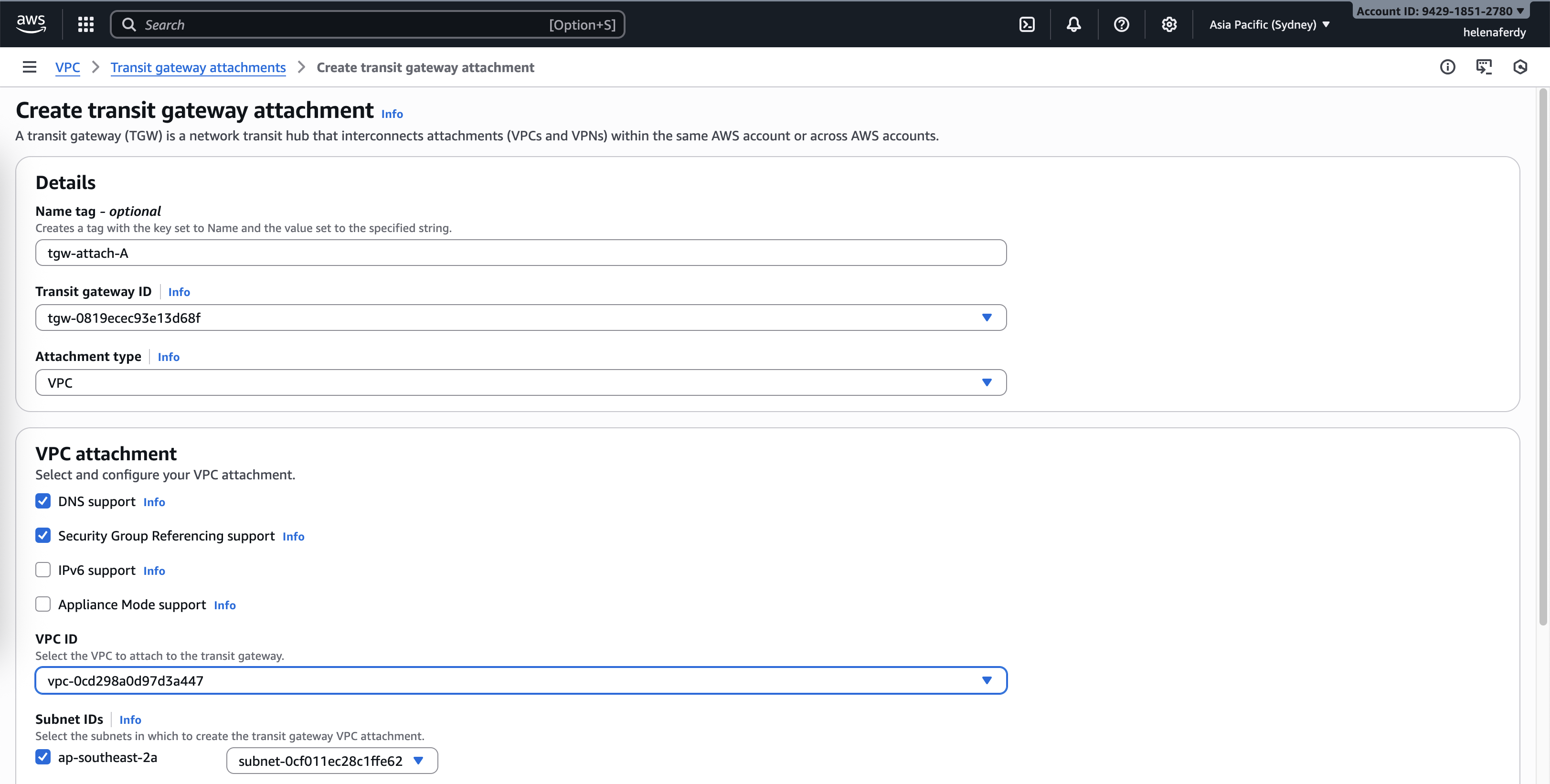
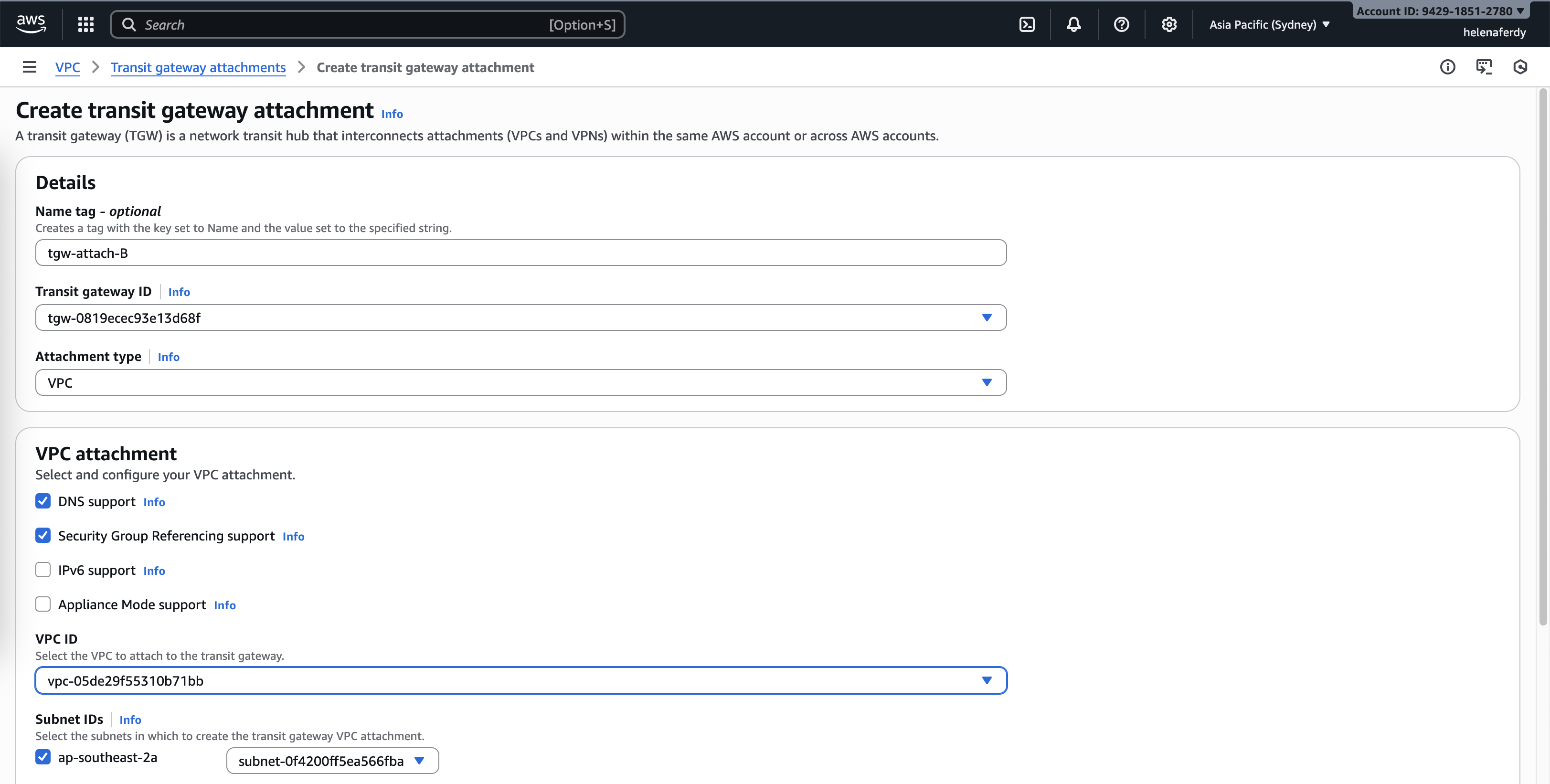
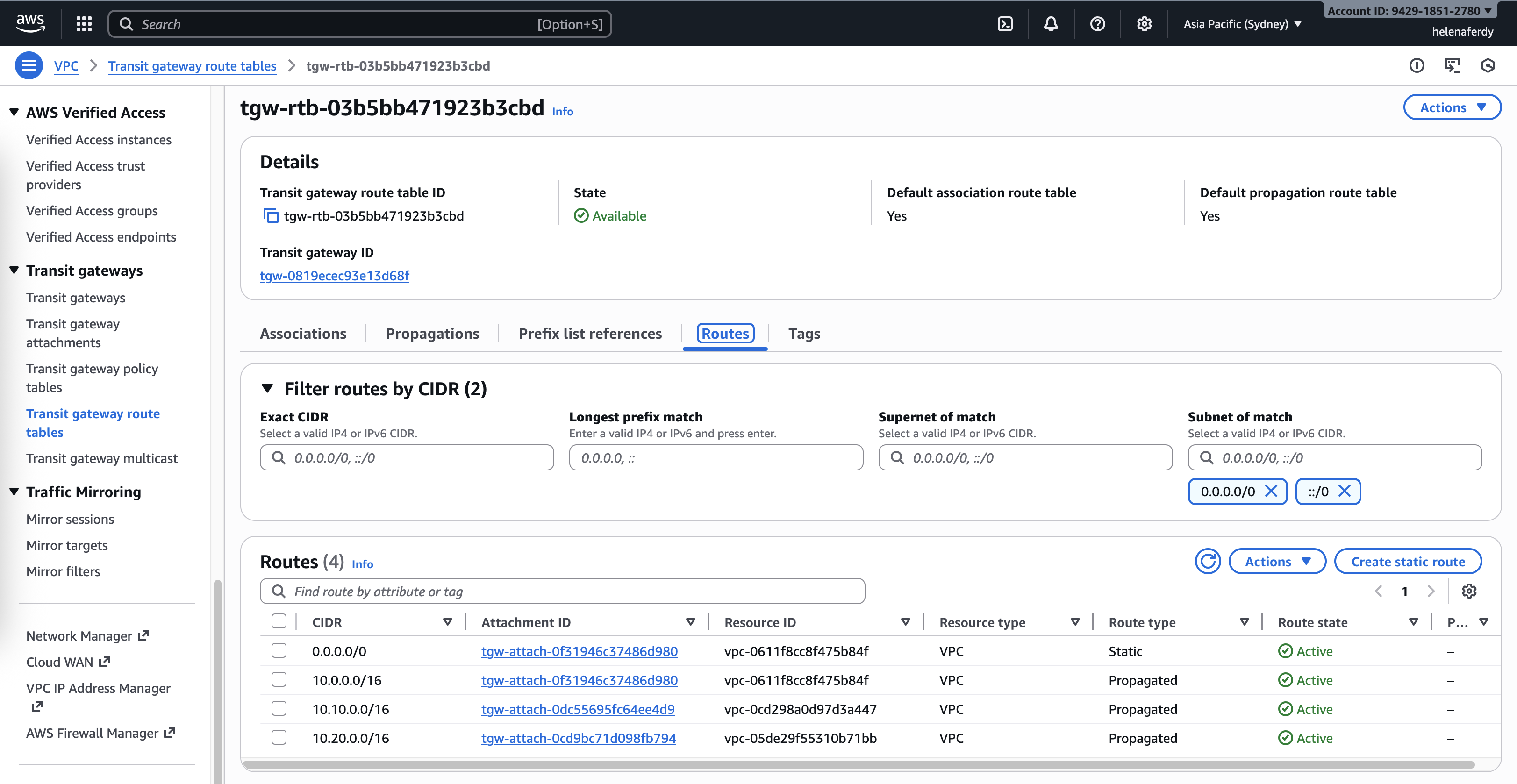
Then we create Transit Gateway Attachments for each VPC
A Transit Gateway attachment is the Layer-3 link between a resource and the Transit Gateway. Common types: VPC attachment, VPN attachment, Direct Connect attachment, and Peering attachment. Each attachment creates an interface on the Transit Gateway that can send/receive routes and forward traffic.
First we create attacment for VPC-A and attach the the VPC and its subnet
Same goes with VPC-B
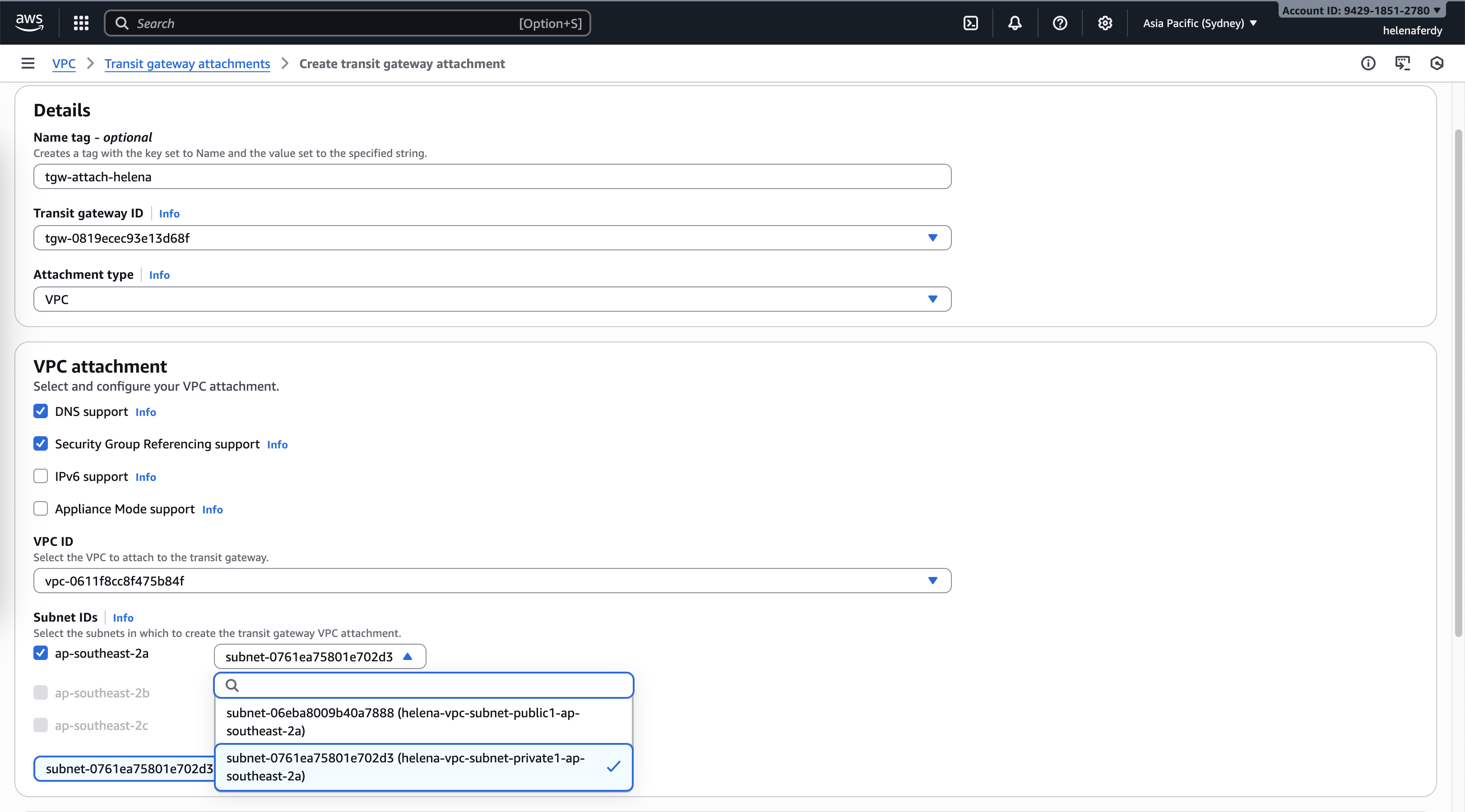
And VPC-Helena where here we will attach the only the private subnet because thats the one facing the Transit Gateway
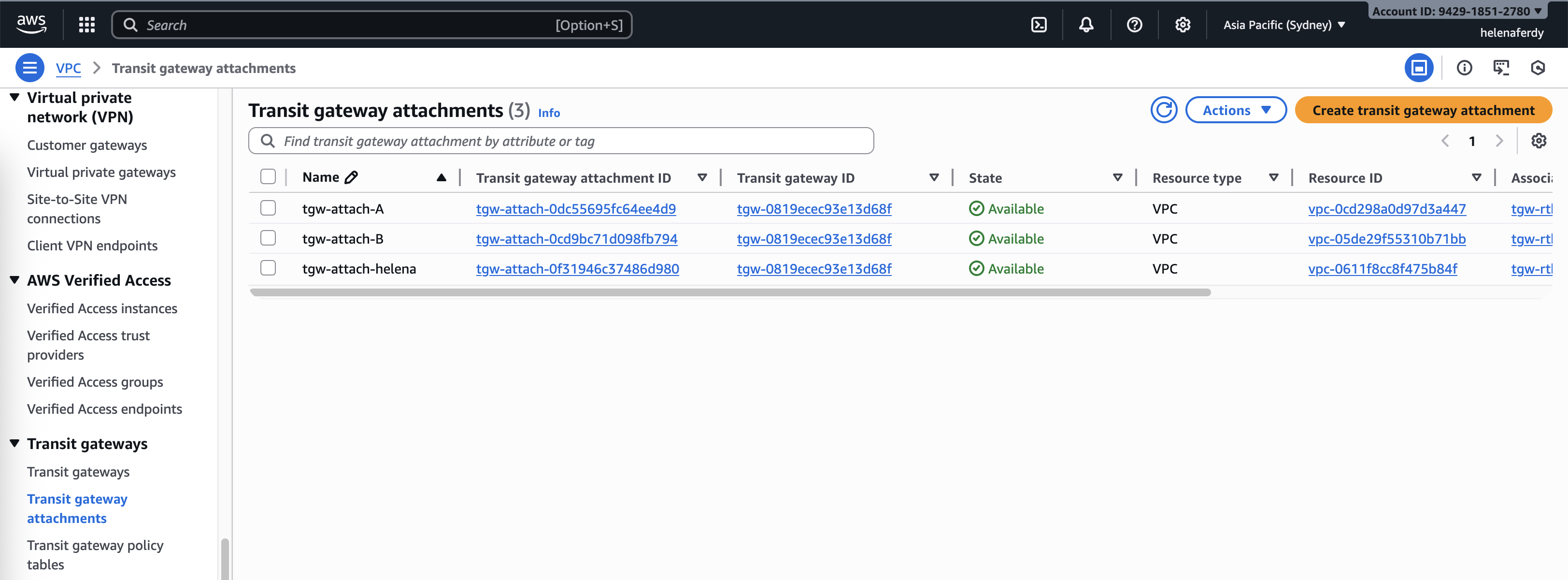
Here after all attachments are configured
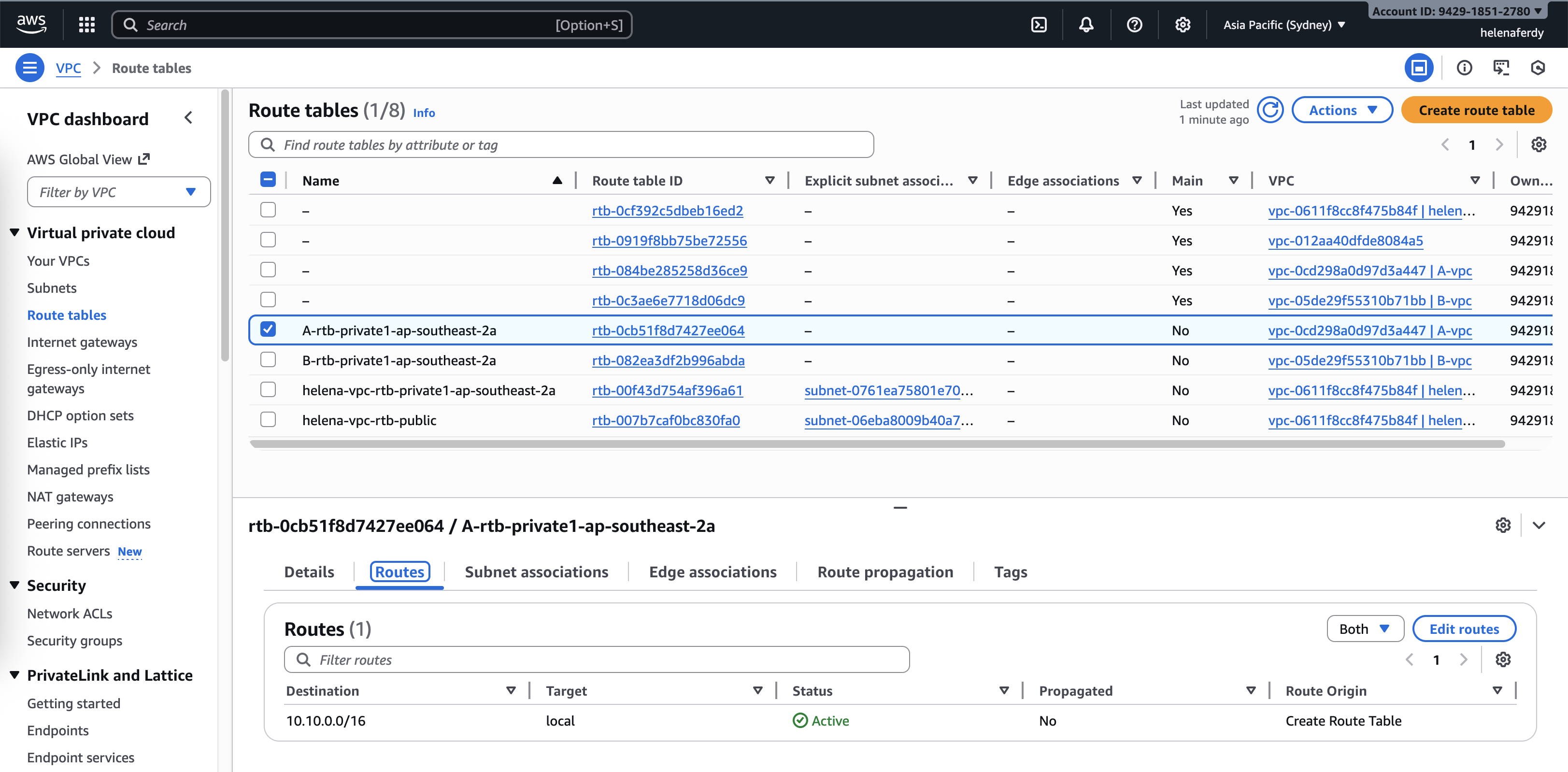
Configuring Routing
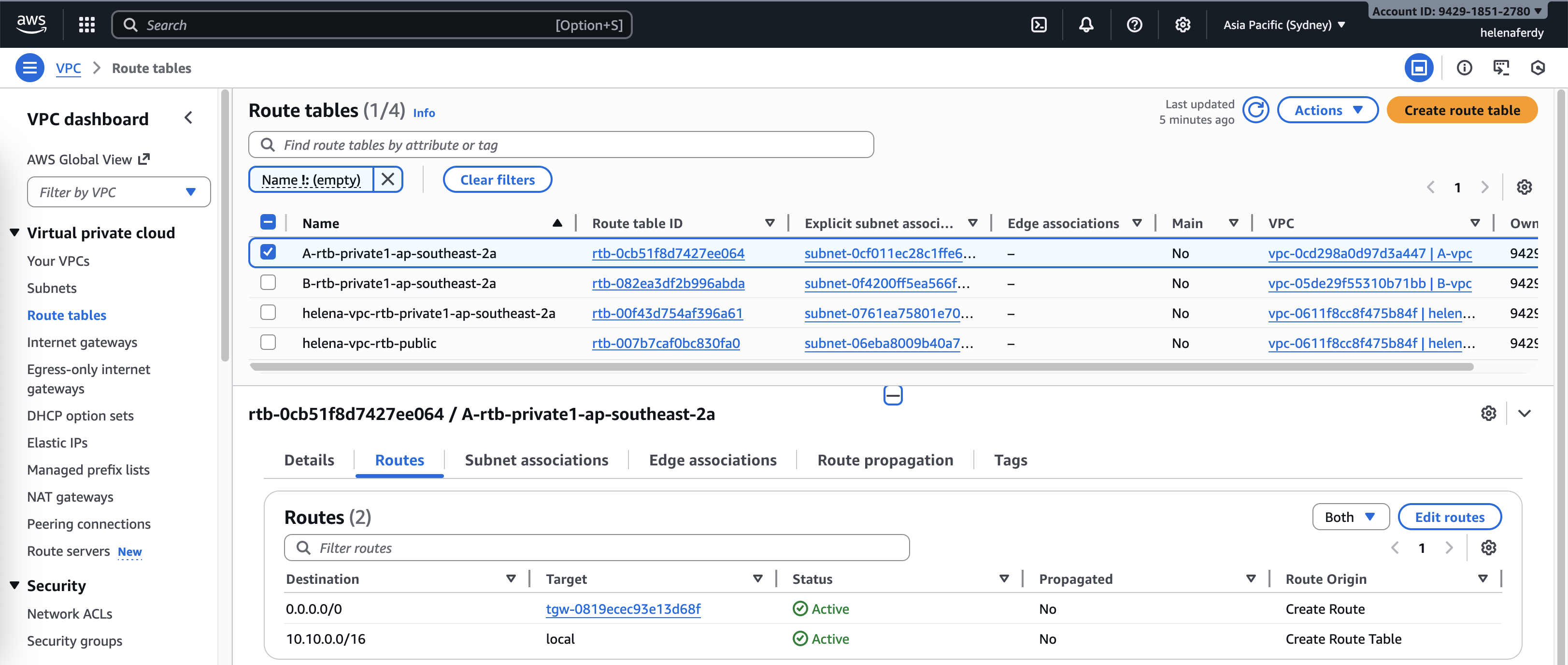
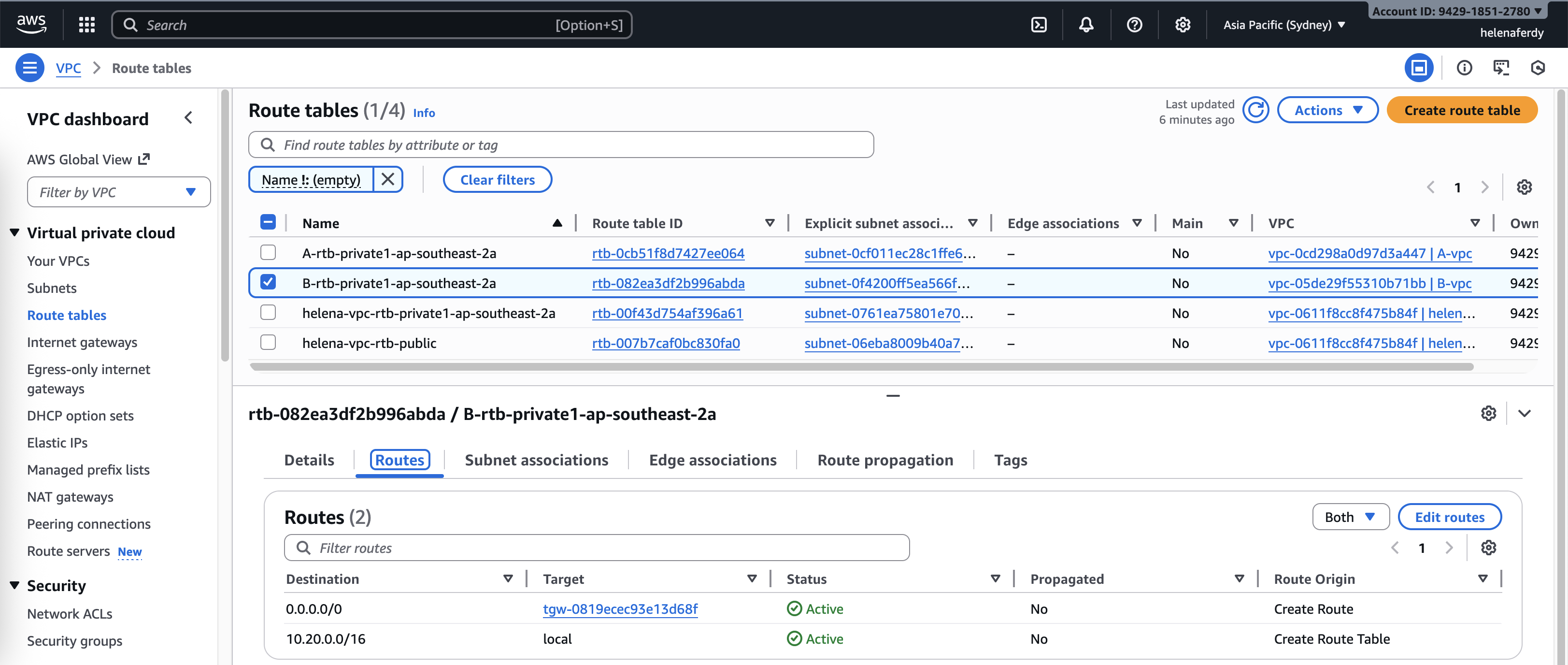
Each VPC holds their own routing table, we need to give them routes to reach the transit gateway, for VPC A & B, we simply add default route to pass all traffic to the Transit Gateway
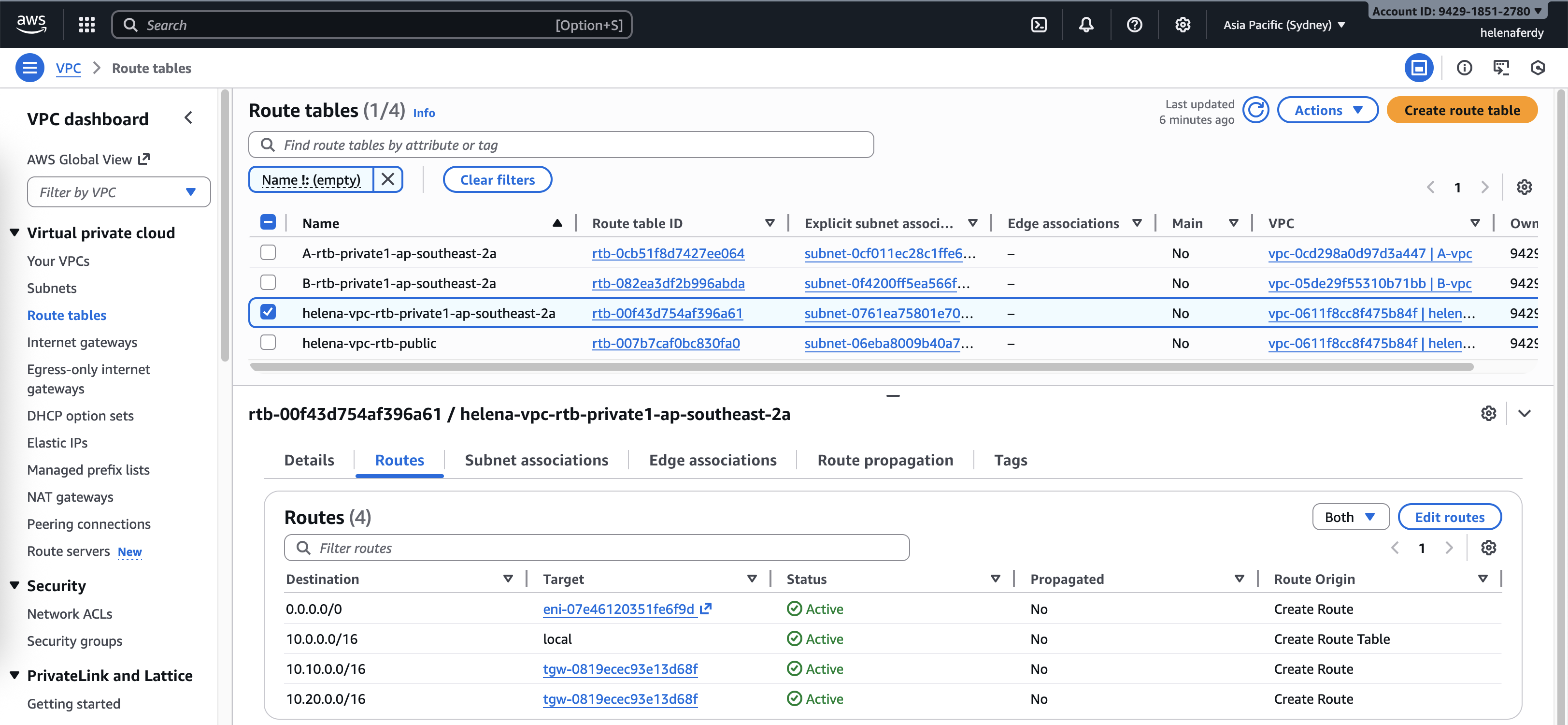
For Helena VPC’s private subnet, we need to make sure it can reach VPC A & B subnets through Transit Gateway, and pass the default route to the Fortigate Firewall
And lastly we need to configure routes on Transit Gateway as well, here we tell it to pass the default route traffic to helena-vpc’s TGW attachment
Testing
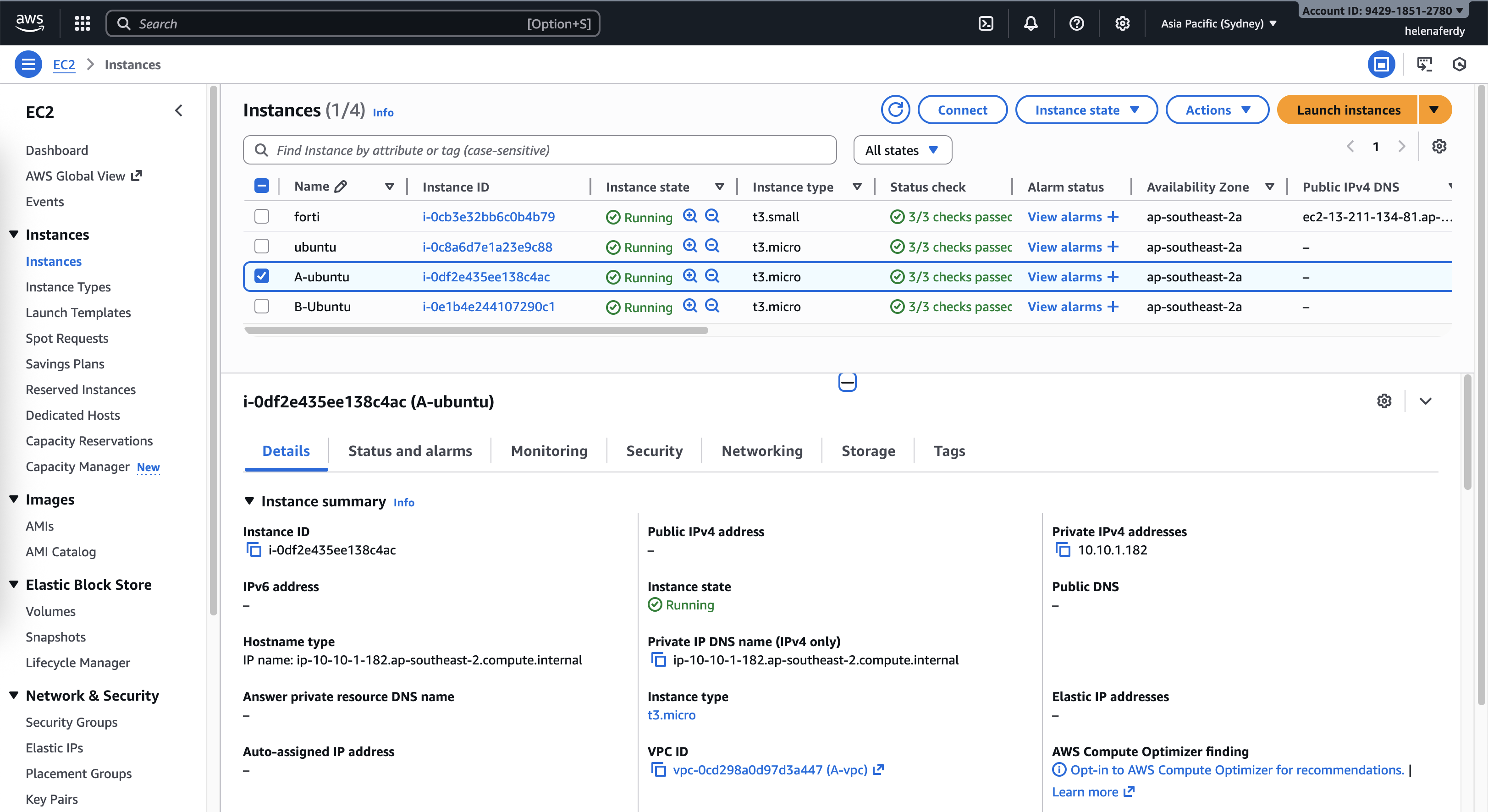
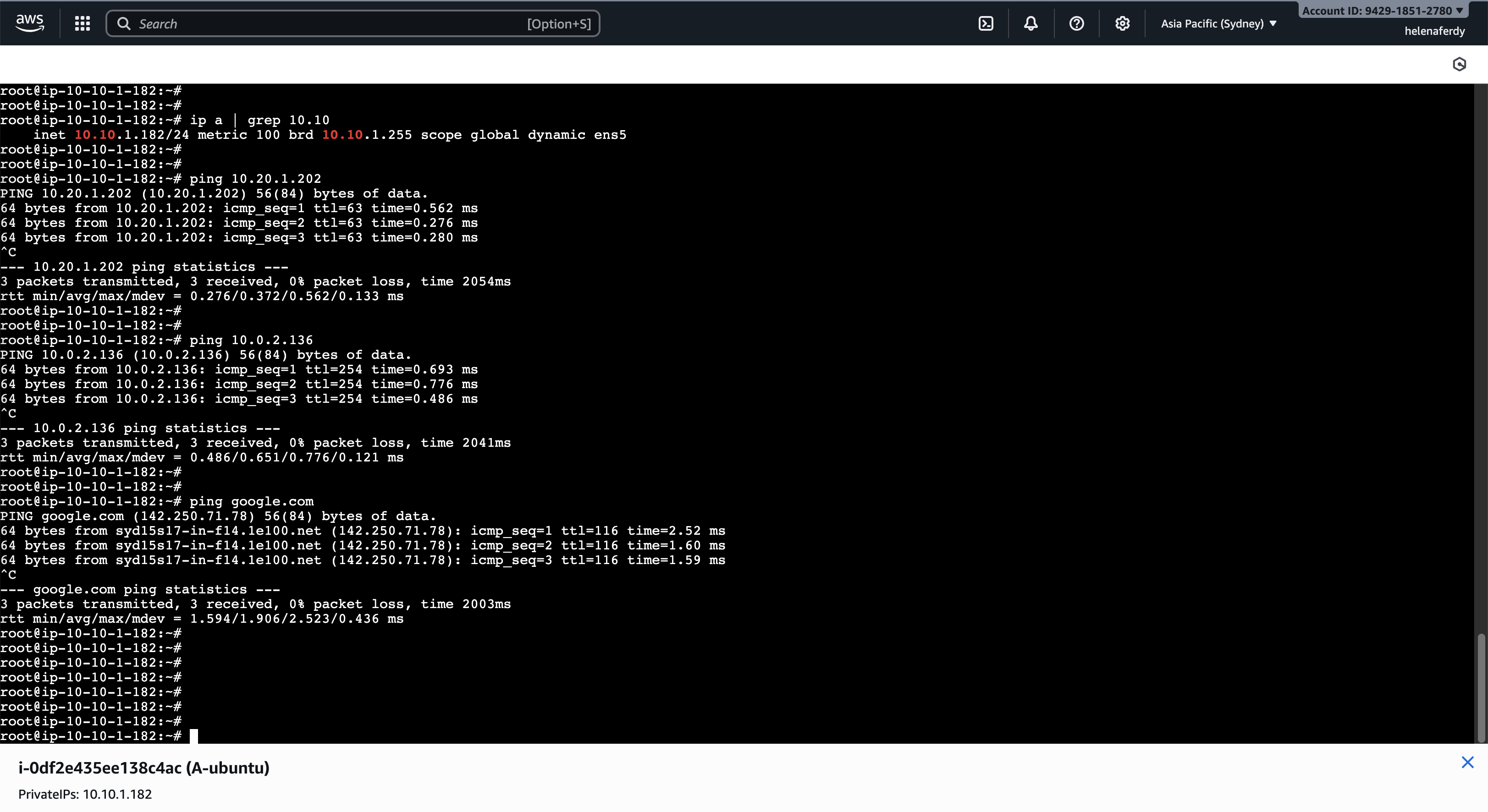
Here we spin up a small linux VM on VPC A with ip of 10.10.1.182
We confirm that this host can access hosts on VPC B, VPC Helena, as well as to Internet through VPC Helena and the firewall configure there
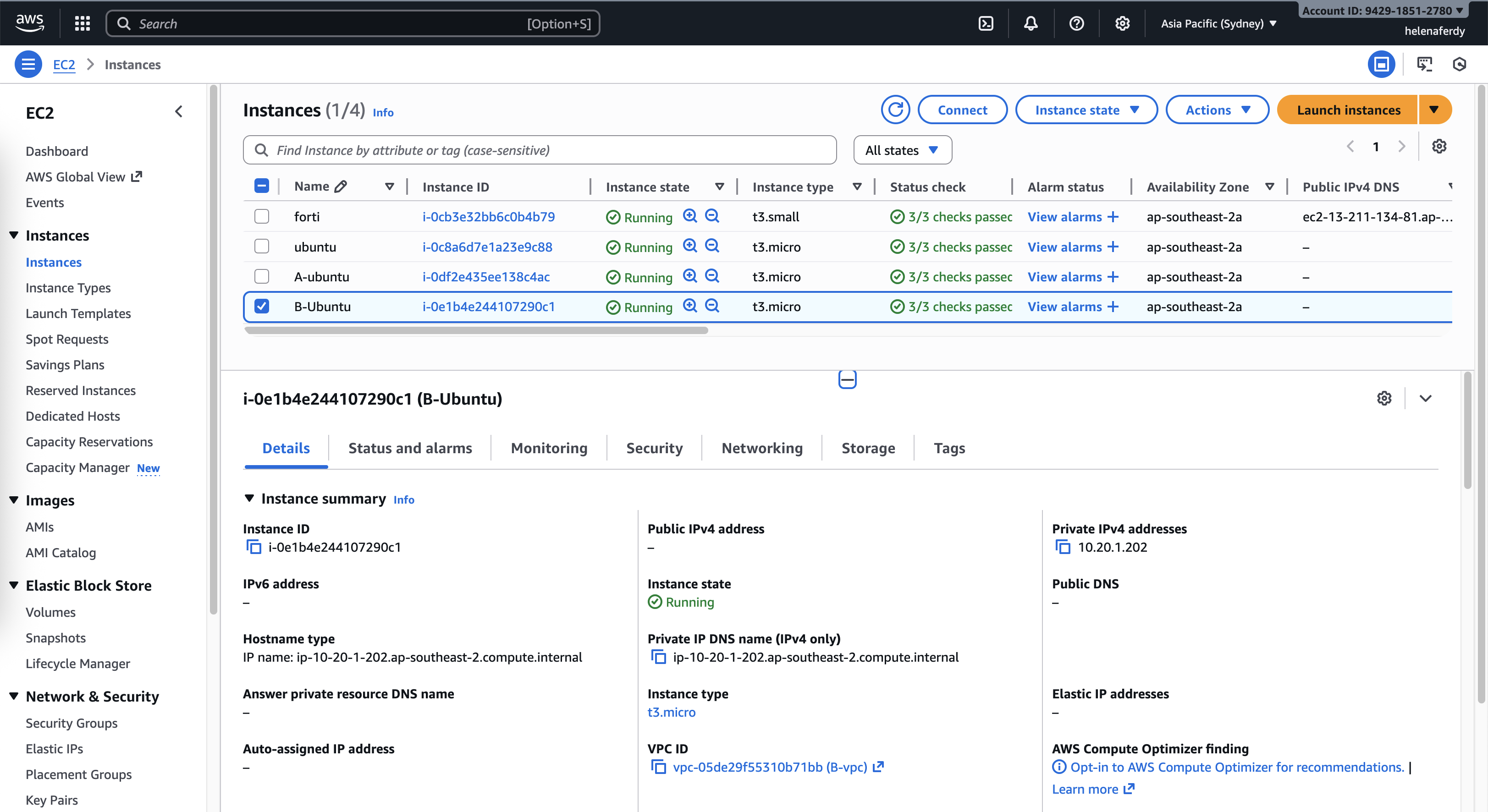
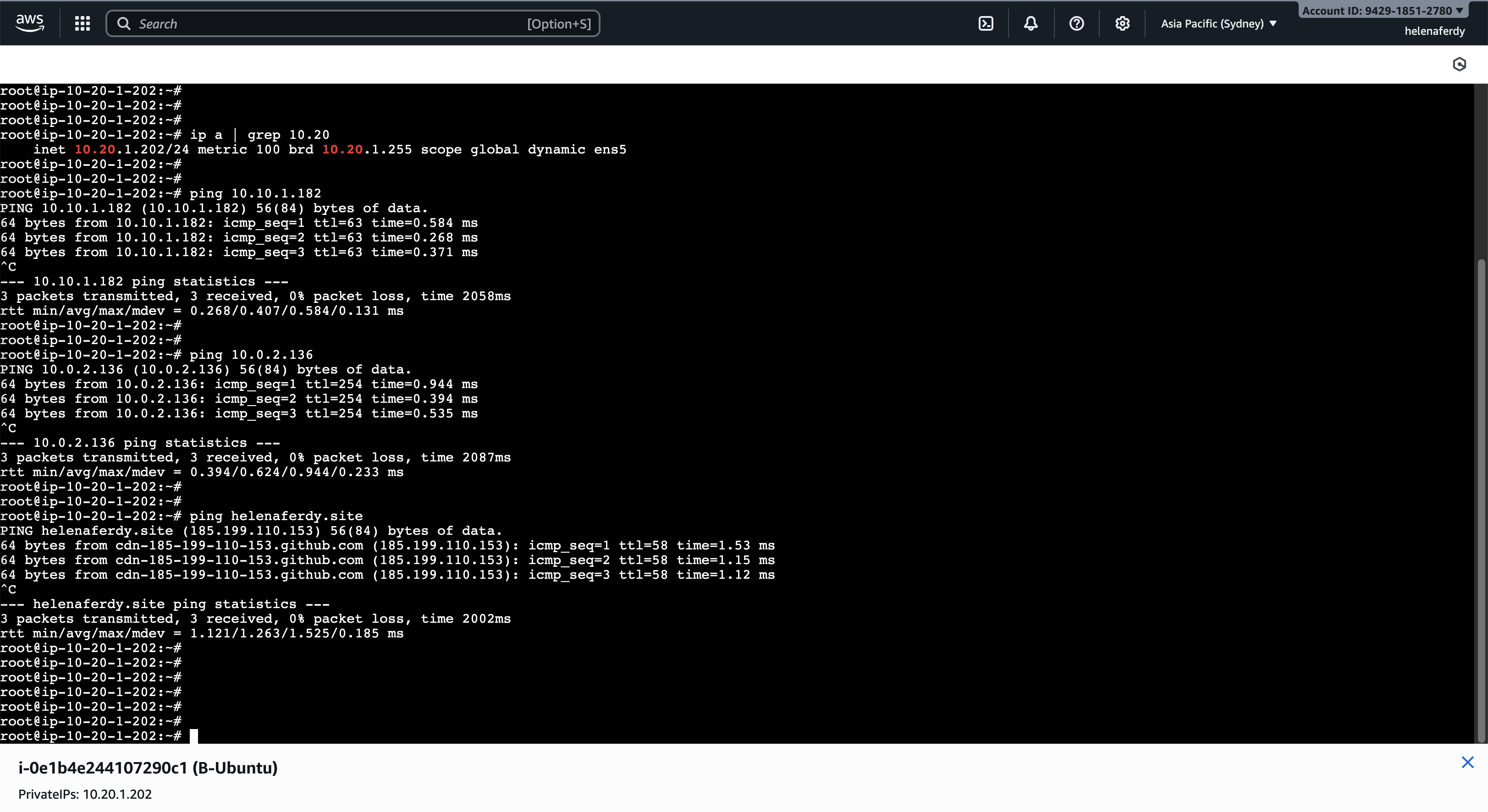
Same goes with the VPC B with ip of 10.20.1.202
This host can also access hosts on VPC A, VPC Helena and the Internet
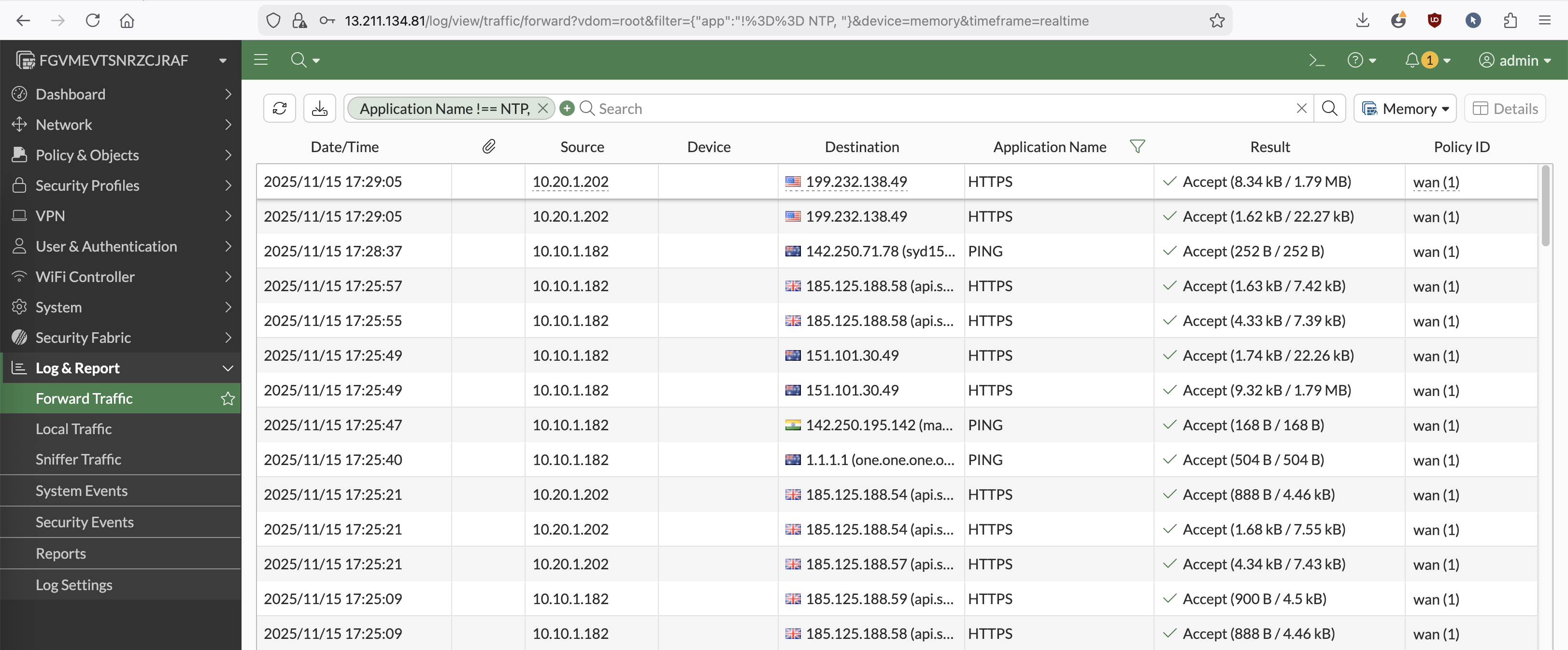
On the Fortigate Firewall, we can see the traffic traversing this device from hosts on VPC A & B to go to the internet