GCP Firewall Endpoint for IPS & URL Filtering
A Firewall Endpoint is a managed, zonal resource within Cloud NGFW Enterprise that performs deep packet inspection (Layer 7) using Palo Alto Networks threat prevention technology. By configuring hierarchical firewall policies to “intercept” and redirect specific traffic flows to this endpoint, we enable inline Intrusion Prevention (IPS) and URL Filtering to block advanced threats and enforce compliance directly within the VPC fabric.
Security Profiles
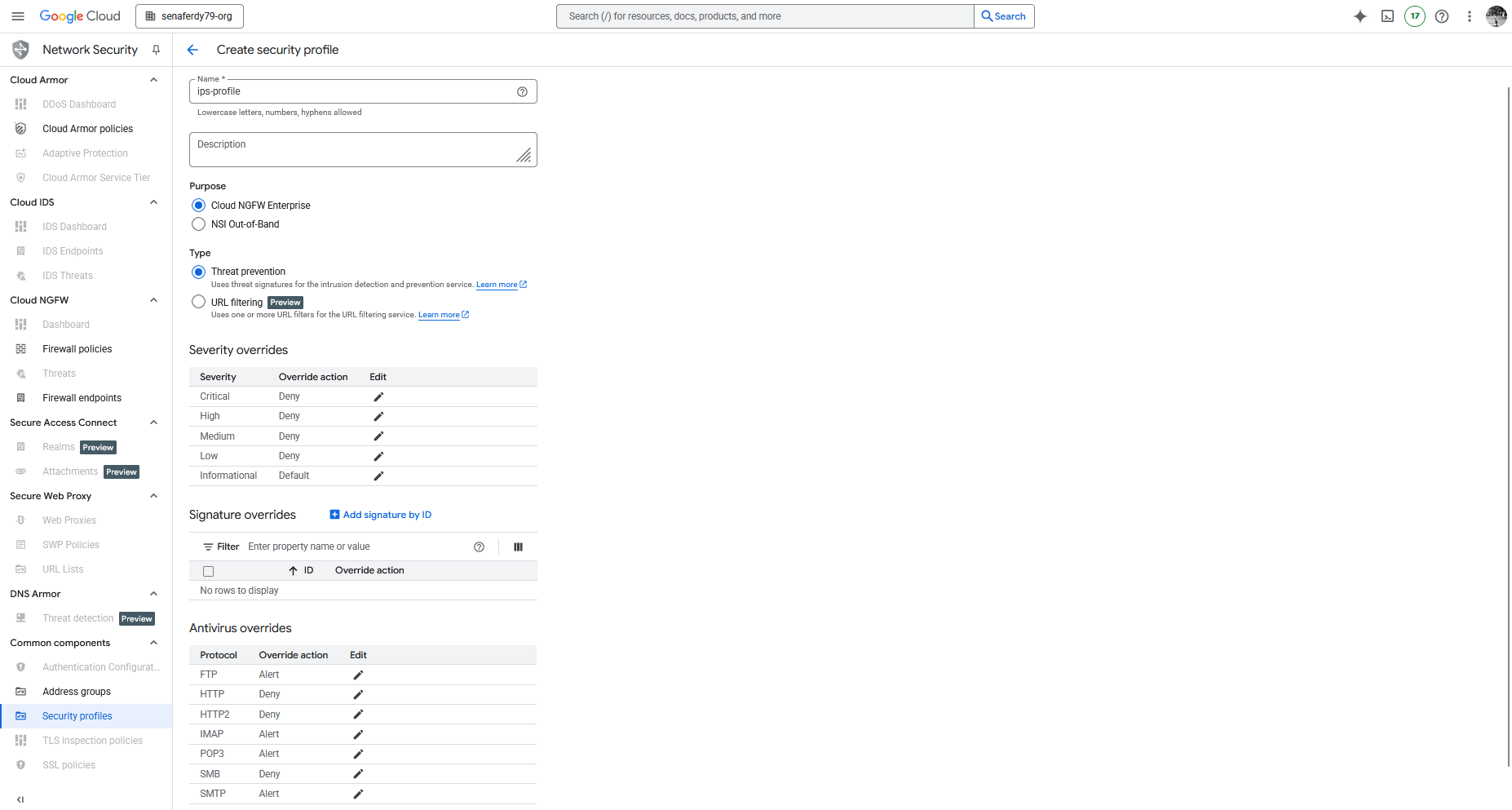
First we need to create Security Profiles, first one is for IPS Profile. Here we set the Deny Override for pretty much every alert apart for Informational
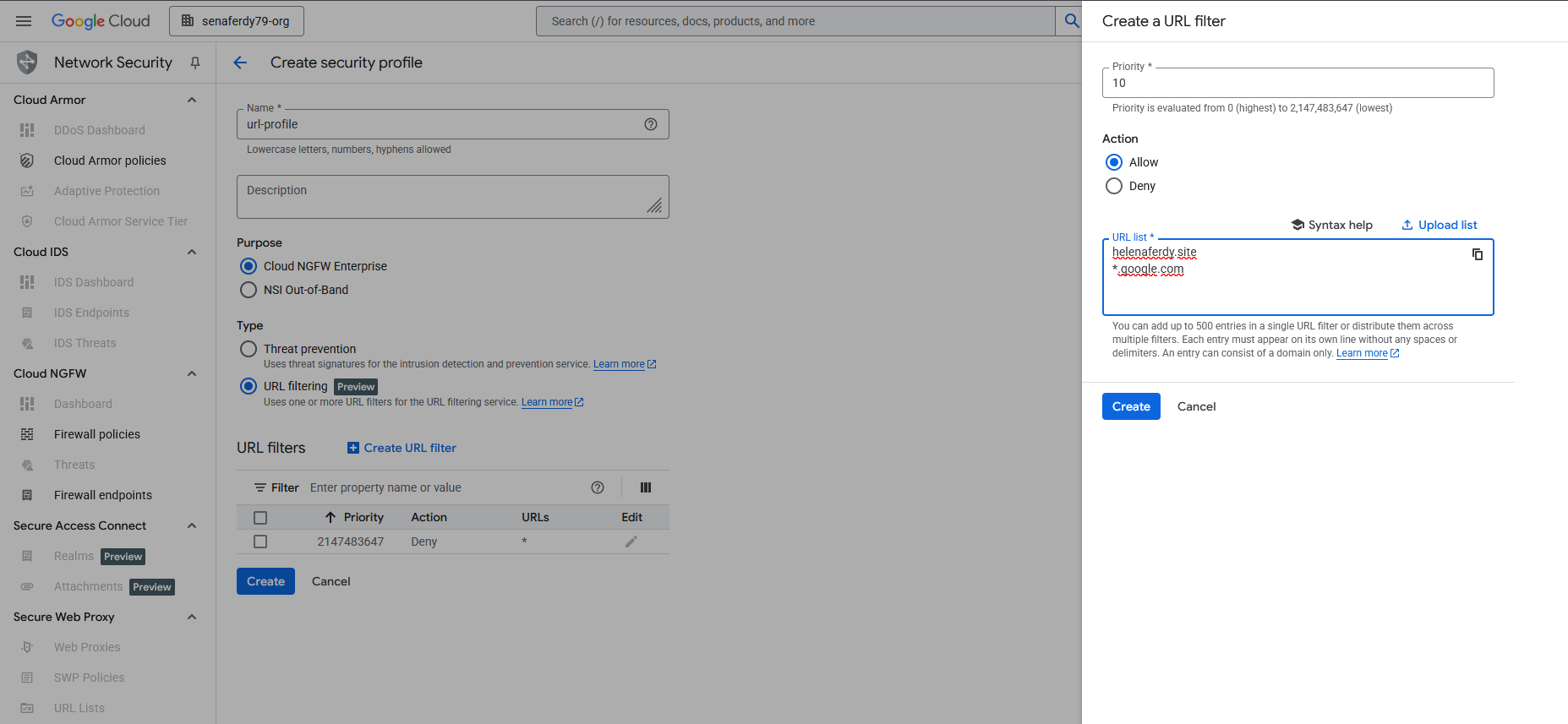
Next we create a URL Filtering Profile, here we’ll whitelist 2 URLs while blocking the rest
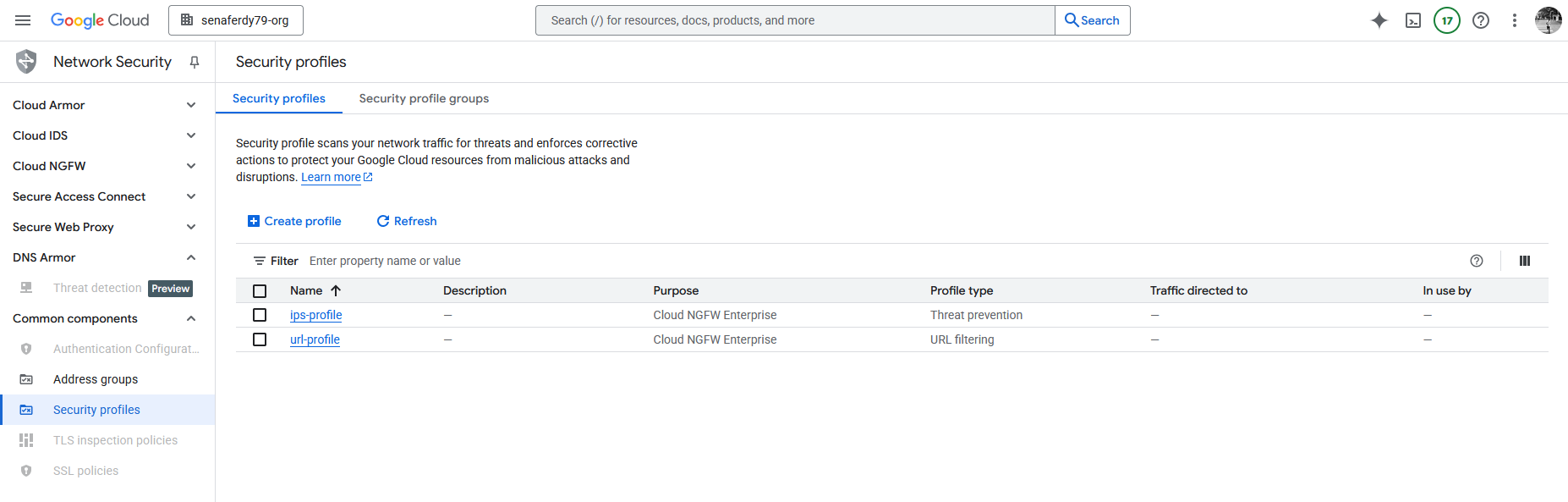
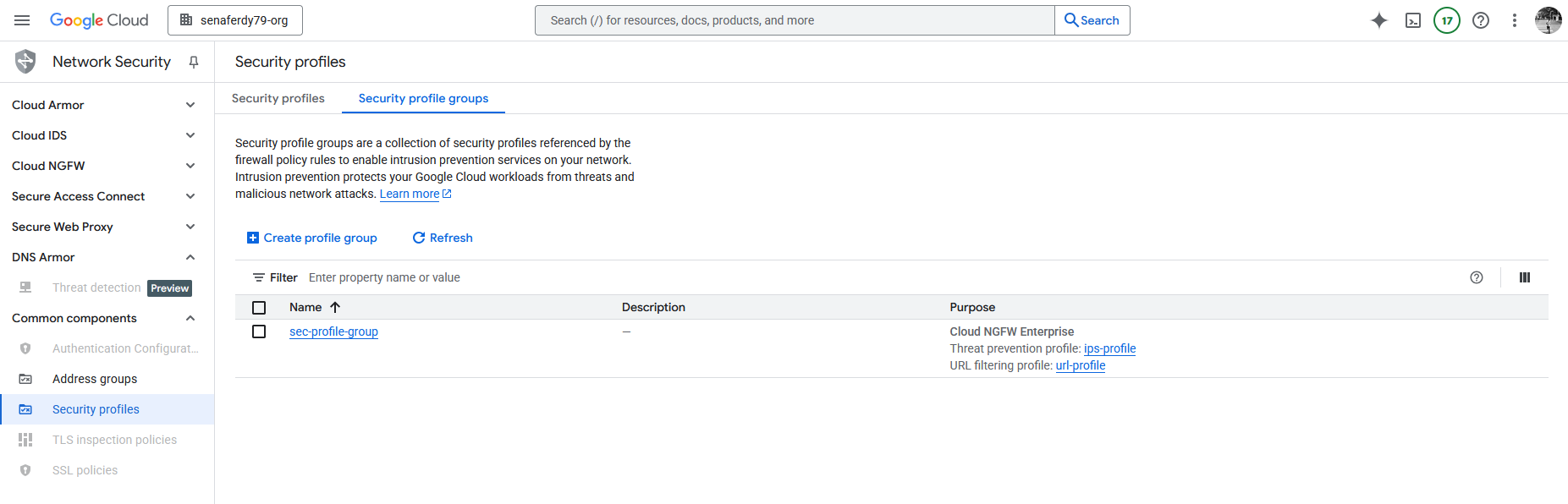
Now we have both our Security Profiles configured
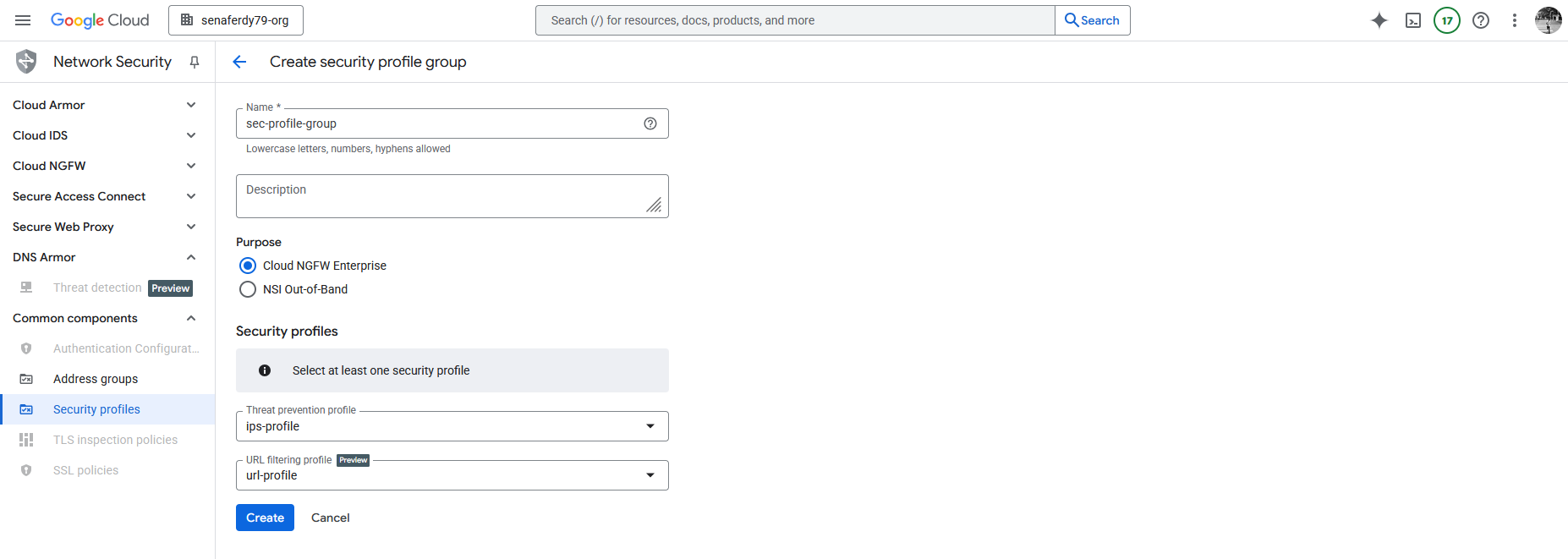
After that we’d need to create a Security Profile Group to contain those 2 profiles
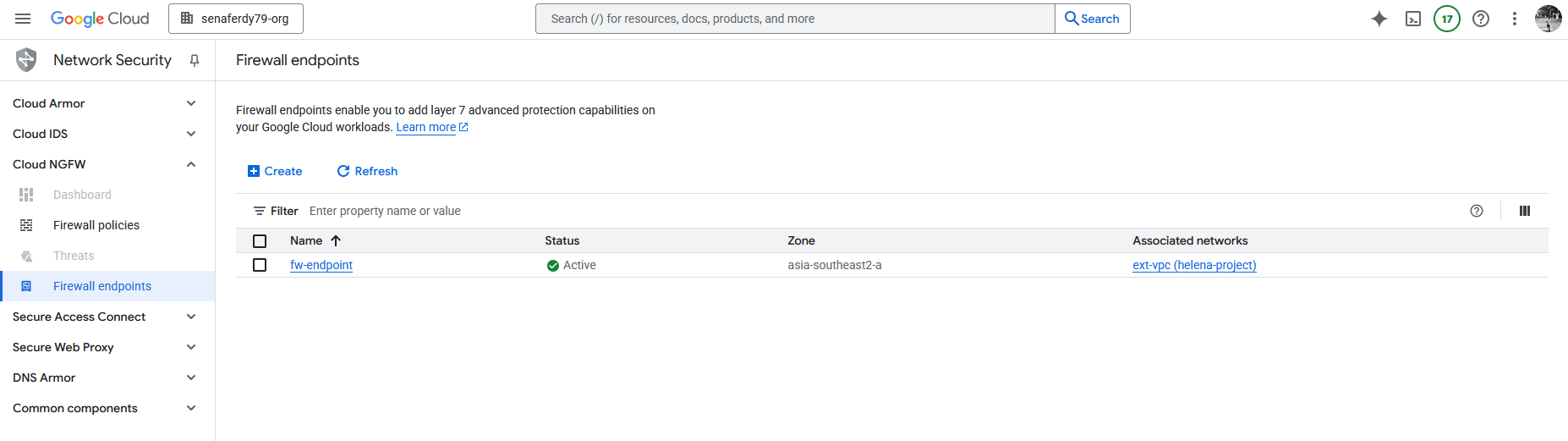
Firewall Endpoint
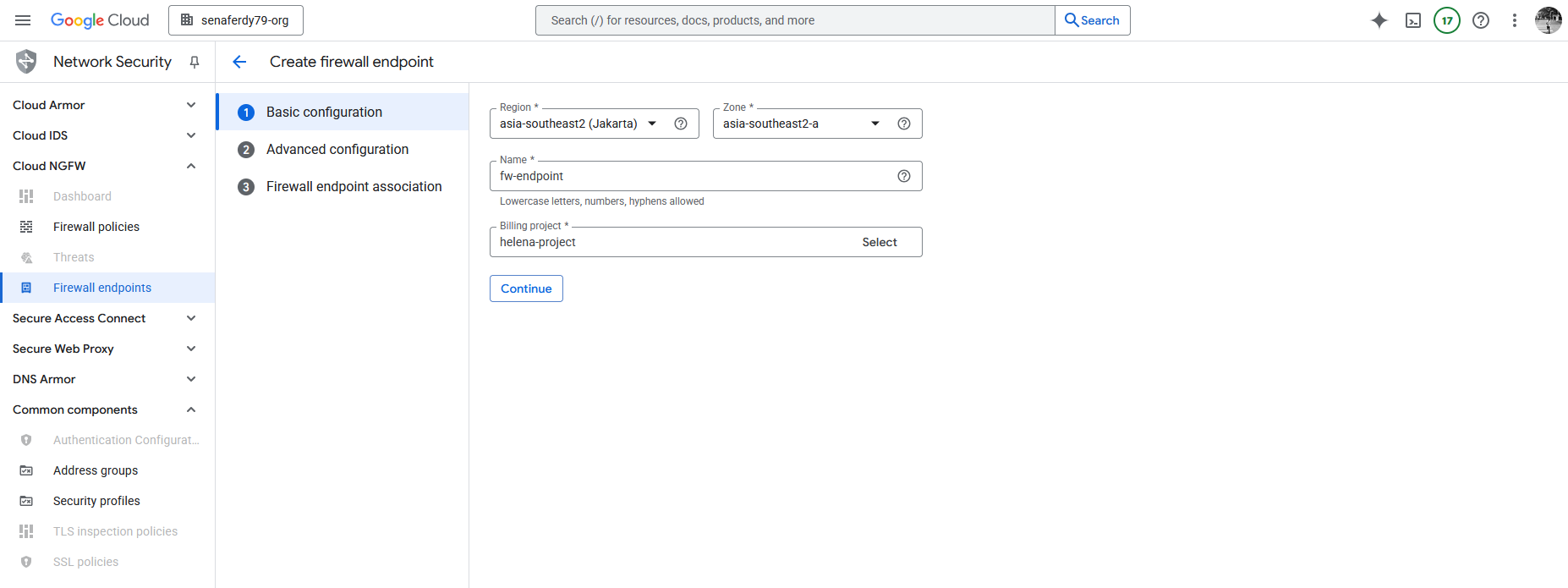
Next we can setup the Firewall Endpoint, here we select the region (FW Endpoint is regional), give it name and select the Billing Project
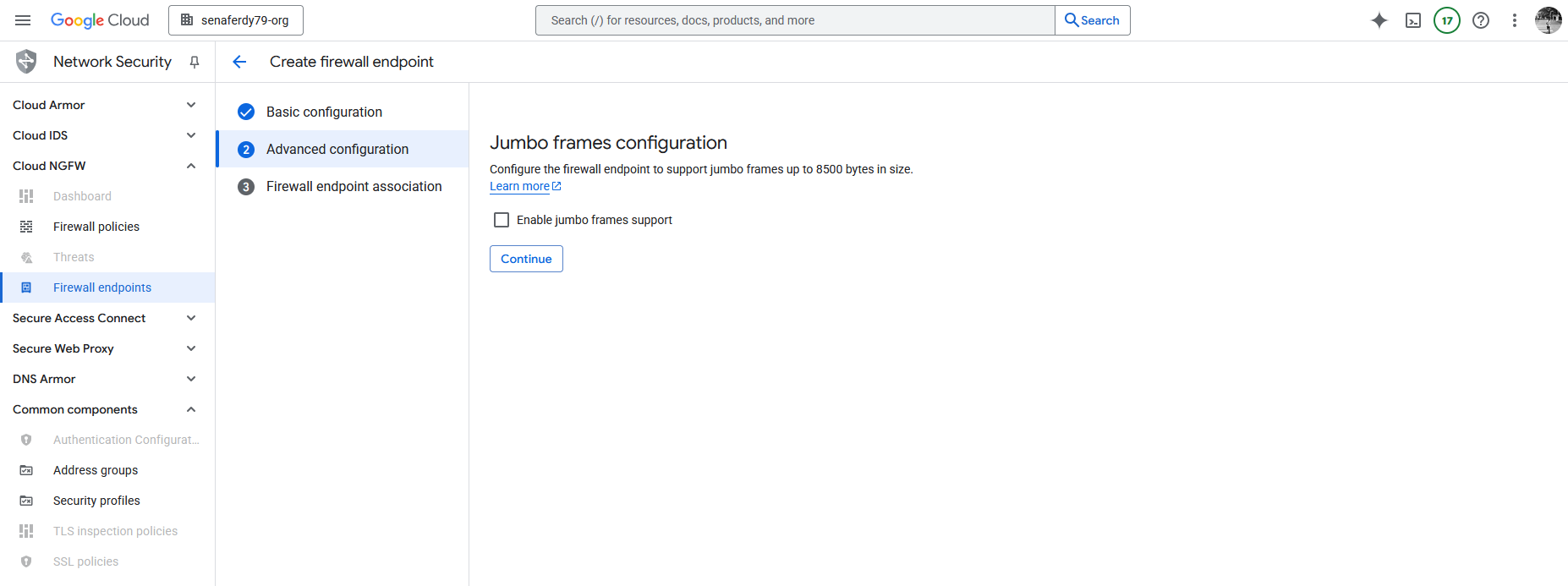
For Jumbo frames we’ll leave the default
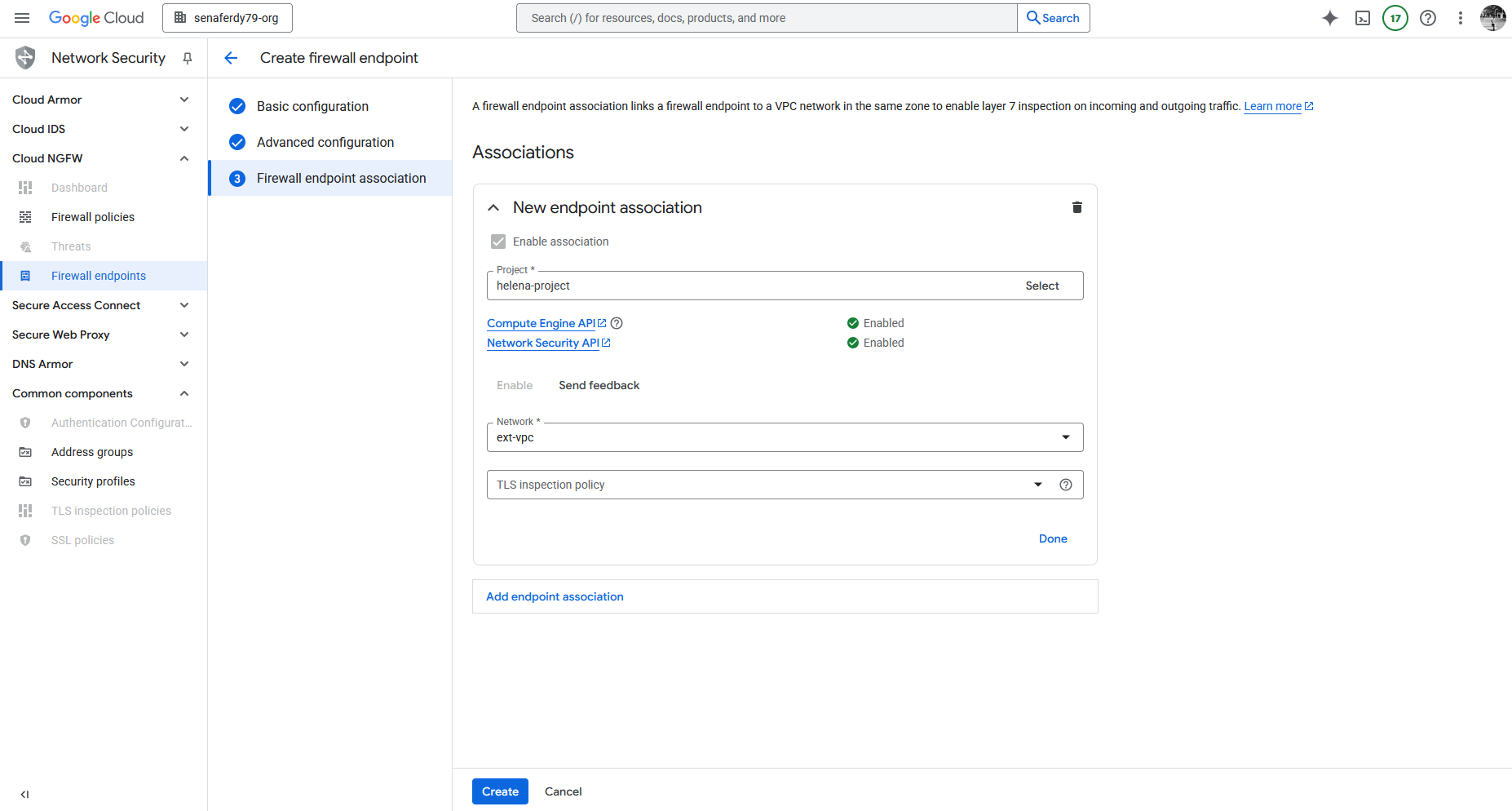
And for association, we’ll associate this FW Endpoint to the ext-vpc, the internet facing VPC, and then hit create
After about 20 minutes, the Firewall Endpoint is now up and running
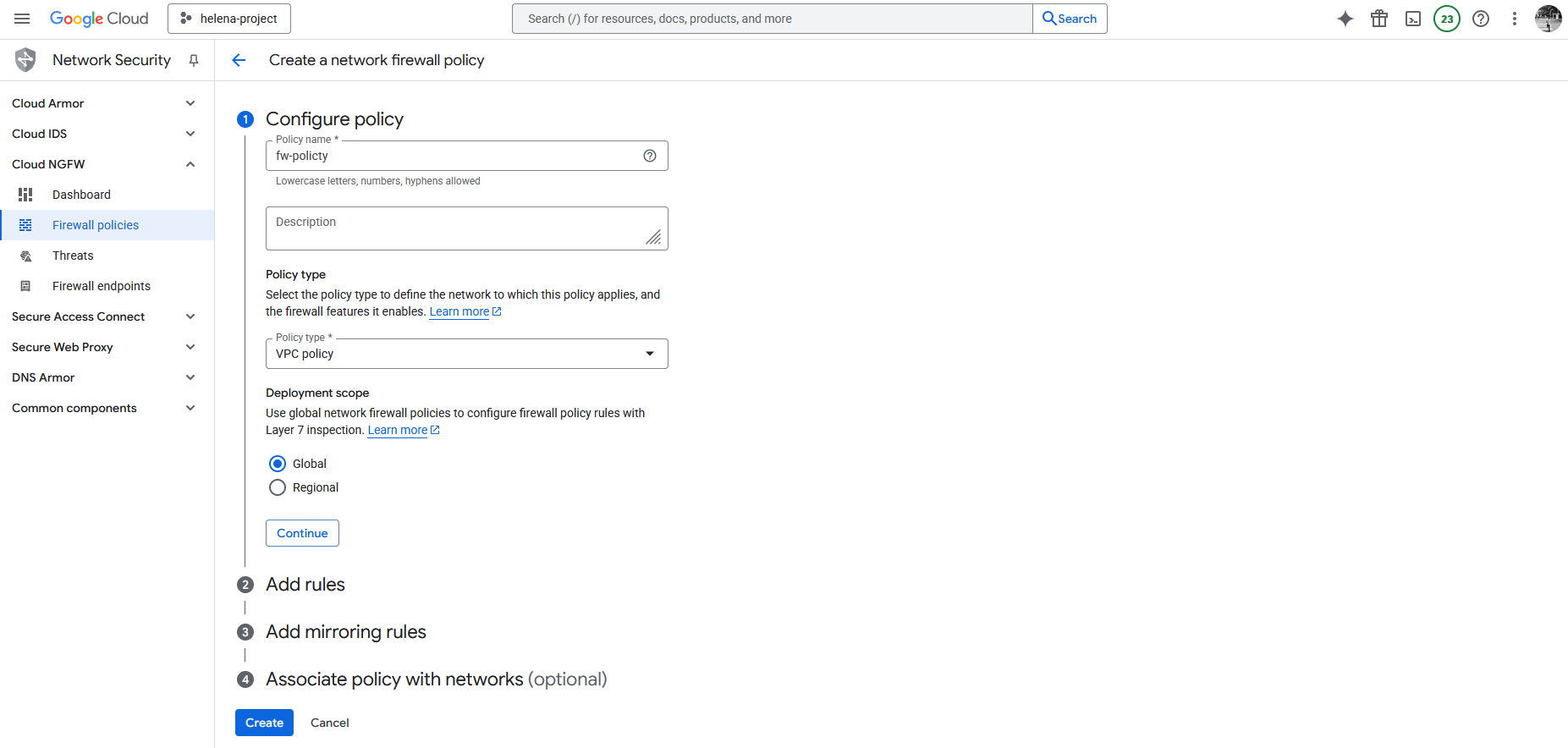
Firewall Policy
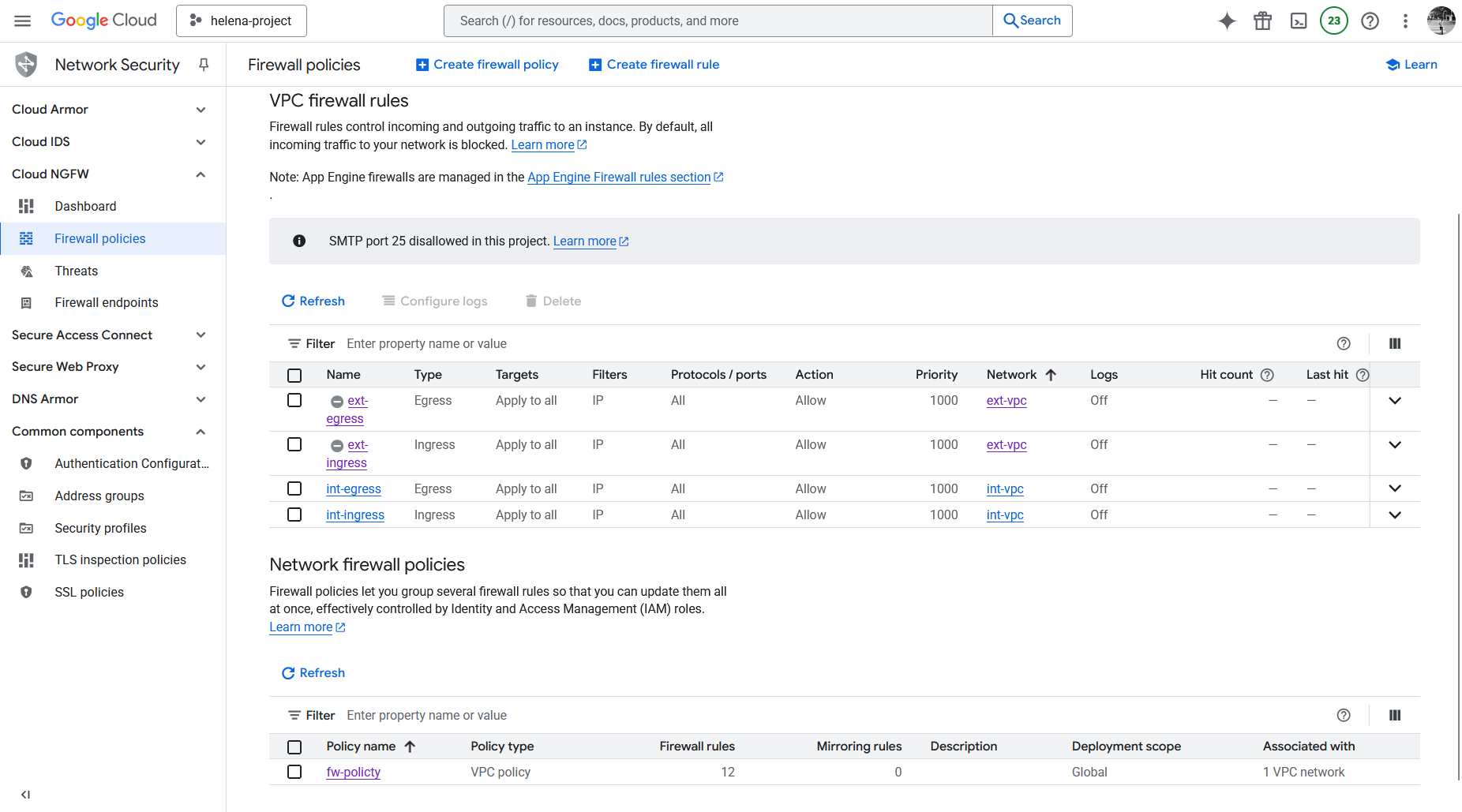
Next we’ll create a Firewall Policy
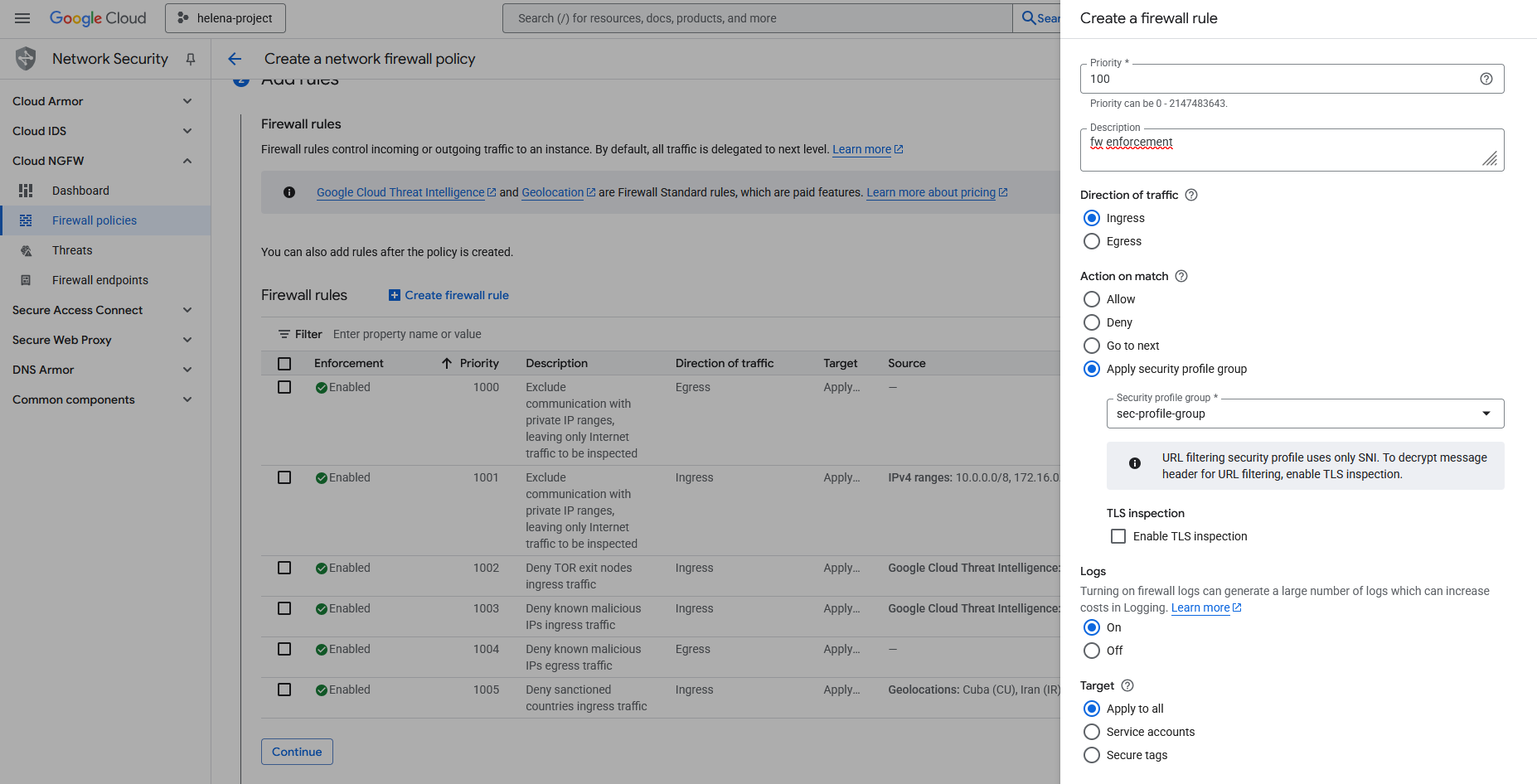
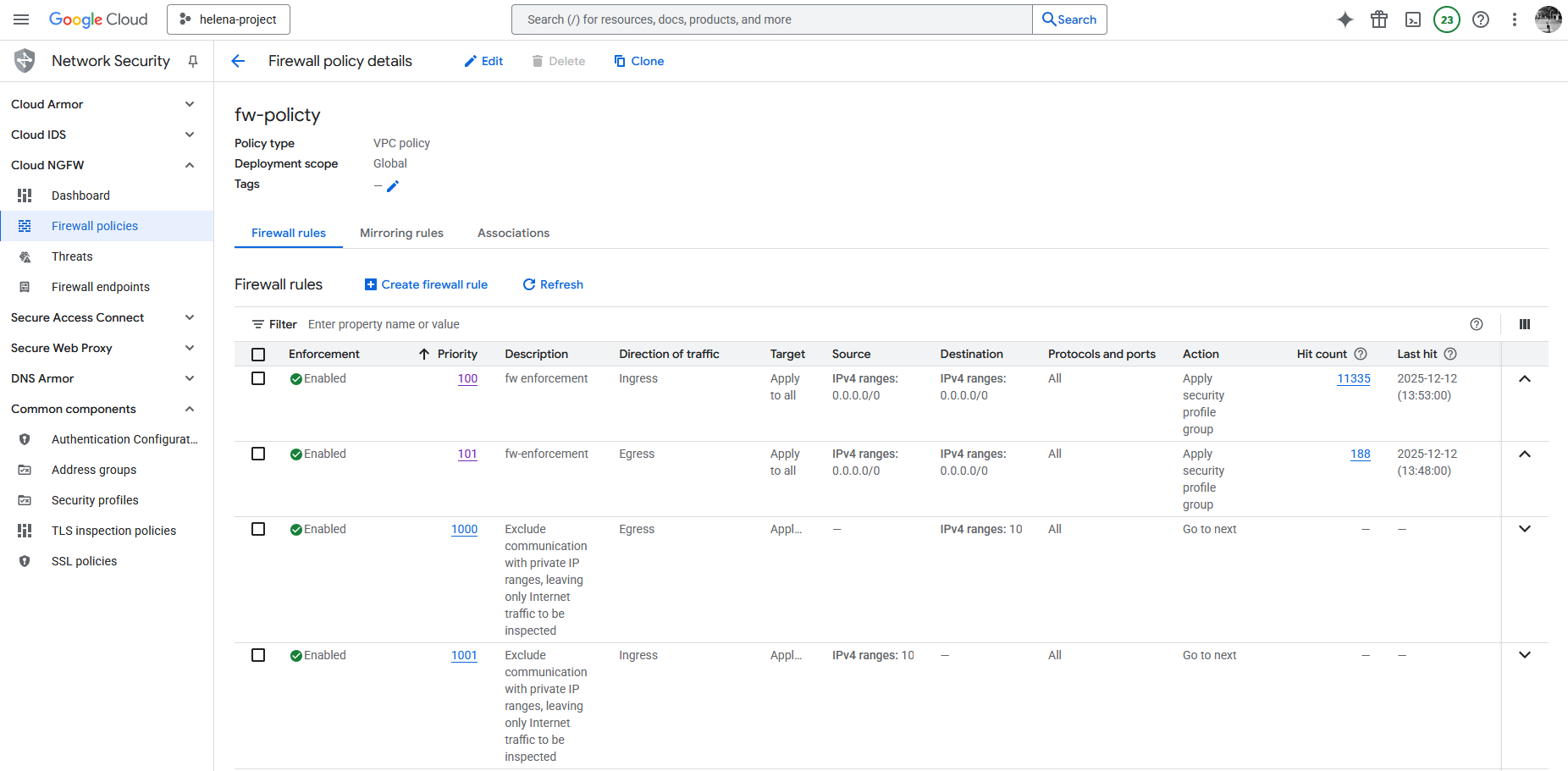
And then create the rules where we attach the Security Profile Groups
For mirroring we’ll leave it as is
And for network association we’ll select our ext-vpc, and then hit create
Here’s the configure Firewall Policy
With 2 rules for egress & ingress applying Security Profile Group for IPS & URL Filtering
Testing
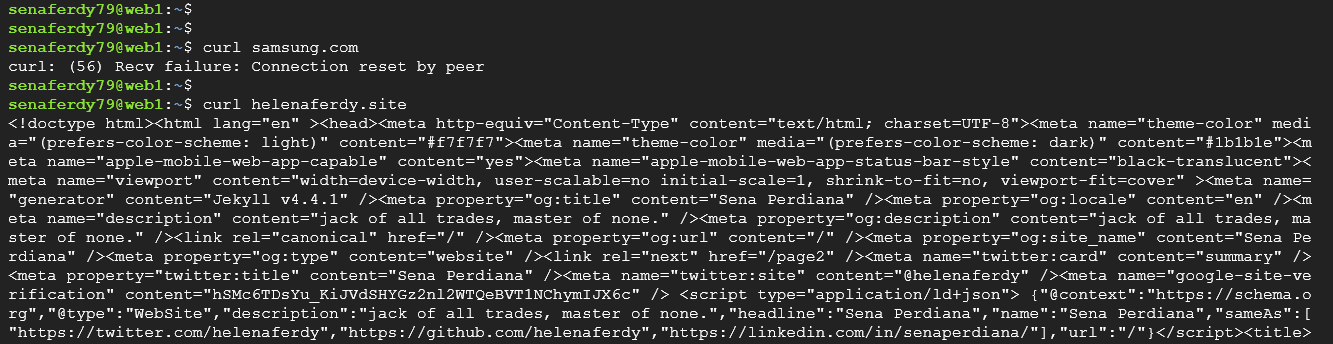
First from a VM inside GCP, we are now only allowed to access the whitelisted URLs while the rest will result in a failure
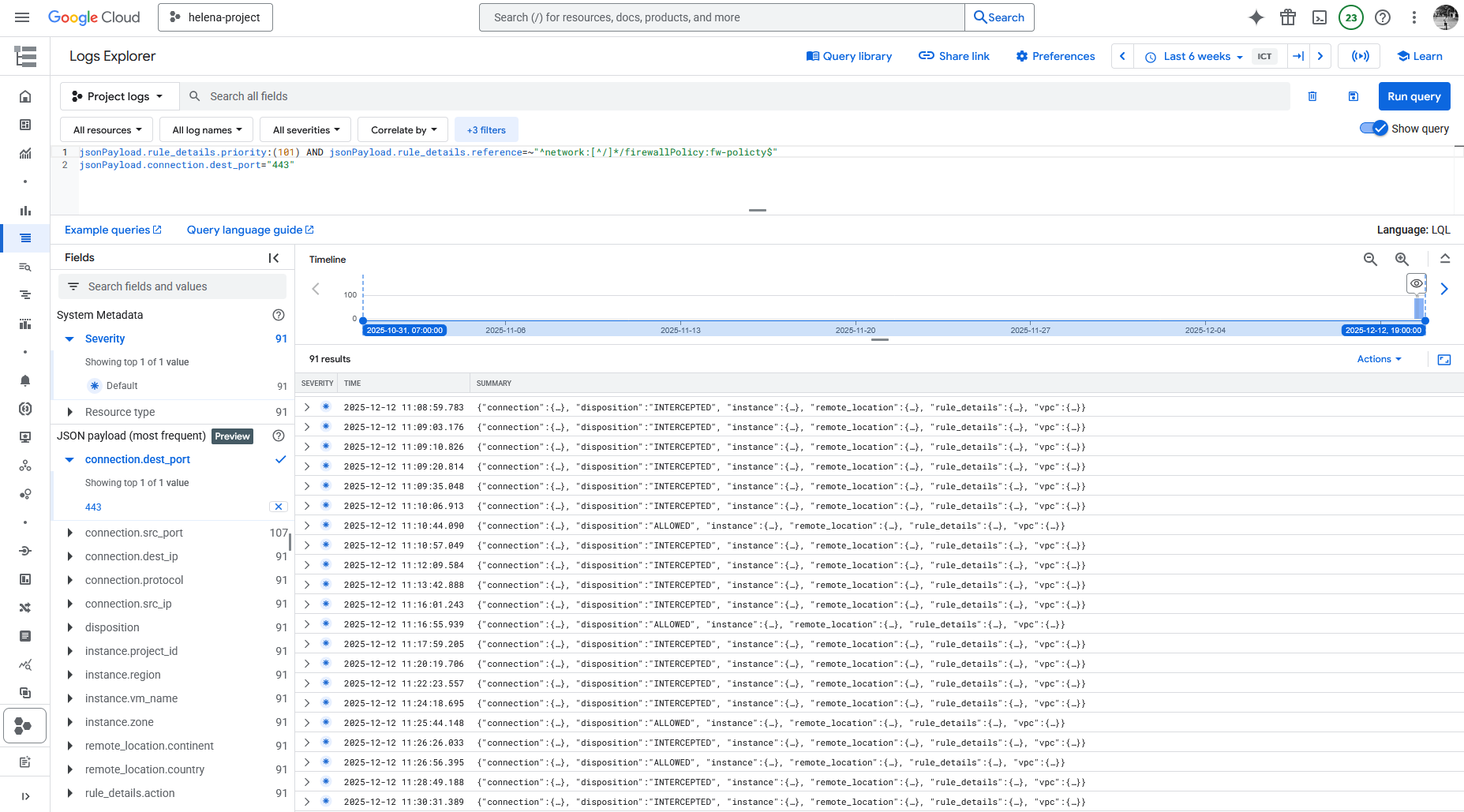
We can see the logs for this event inside the firewall policy
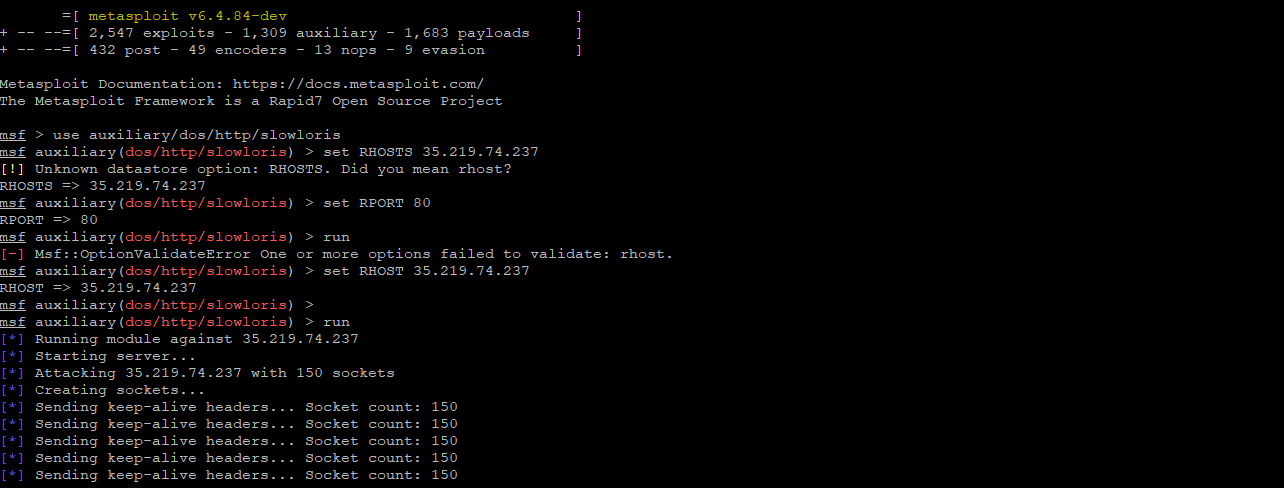
And for testing the IPS, we will try to attach the VM inside GCP from outside network, here we use a Kali Linux to send a simple Denial of Service (DOS) attack by attempting to exhaust the VM’s connection pool by keeping sockets open
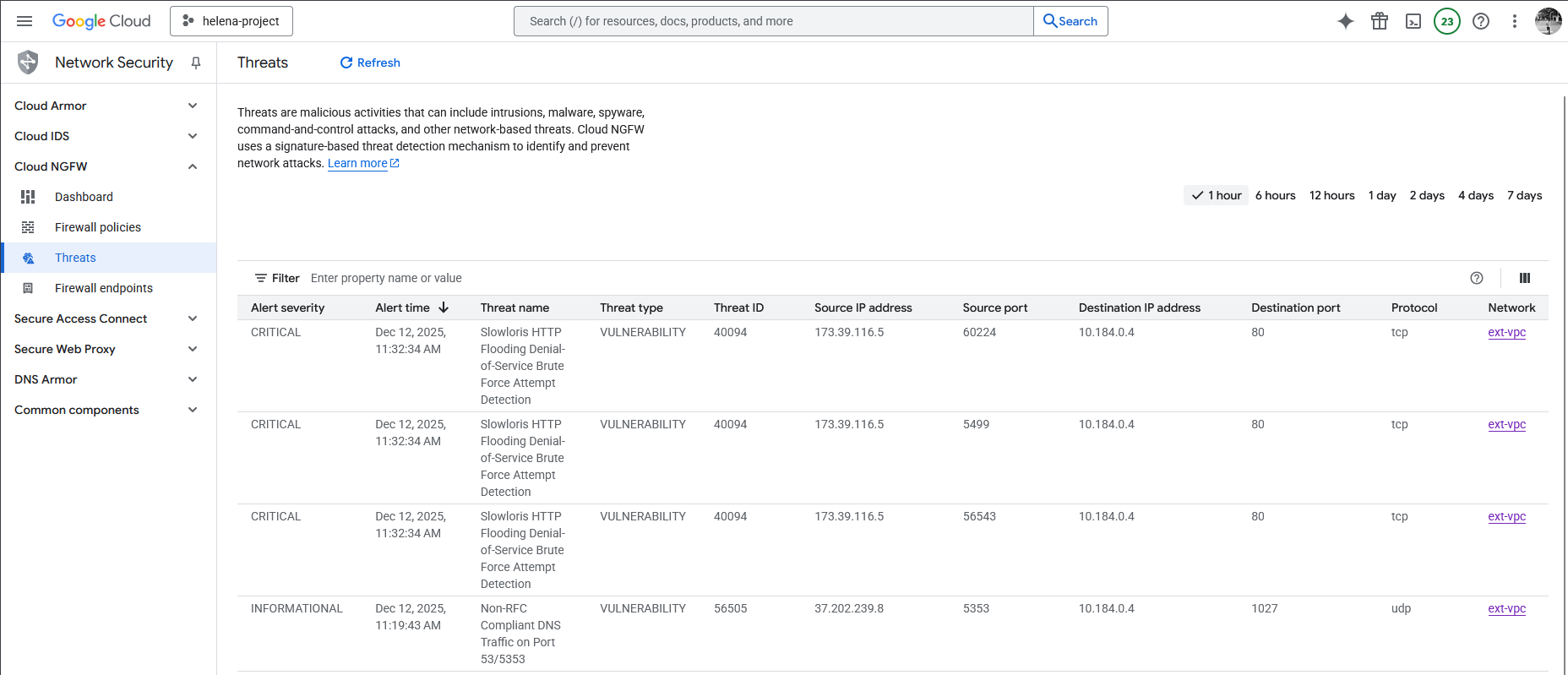
On the GCP Threat Events, we can see that the Firewall Endpoint has successfully identified and prevented this attack