GCP HA VPN with Check Point
In this lab, we build a route-based HA VPN between GCP and a Check Point Firewall, using VTI and eBGP to exchange routes dynamically. Unlike Classic VPN, which is a policy-based VPN that uses encryption domains to define interesting traffic, HA VPN uses dynamic routing with Cloud Router and BGP to advertise and learn prefixes automatically.
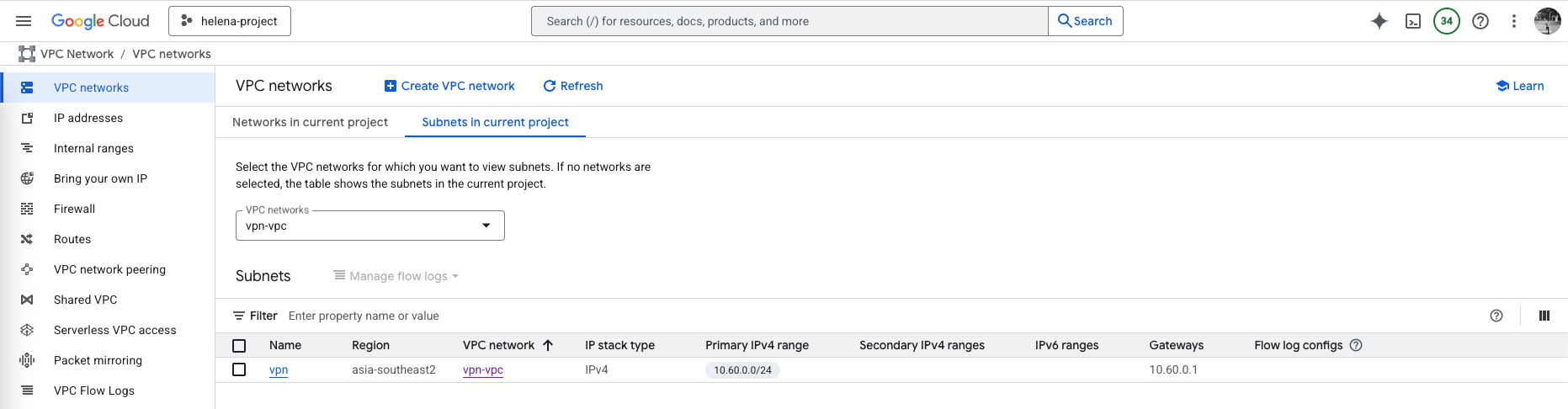
Configuring VPC
Here we’ll use the VPN-VPC on the 10.60.0.0/24 subnet
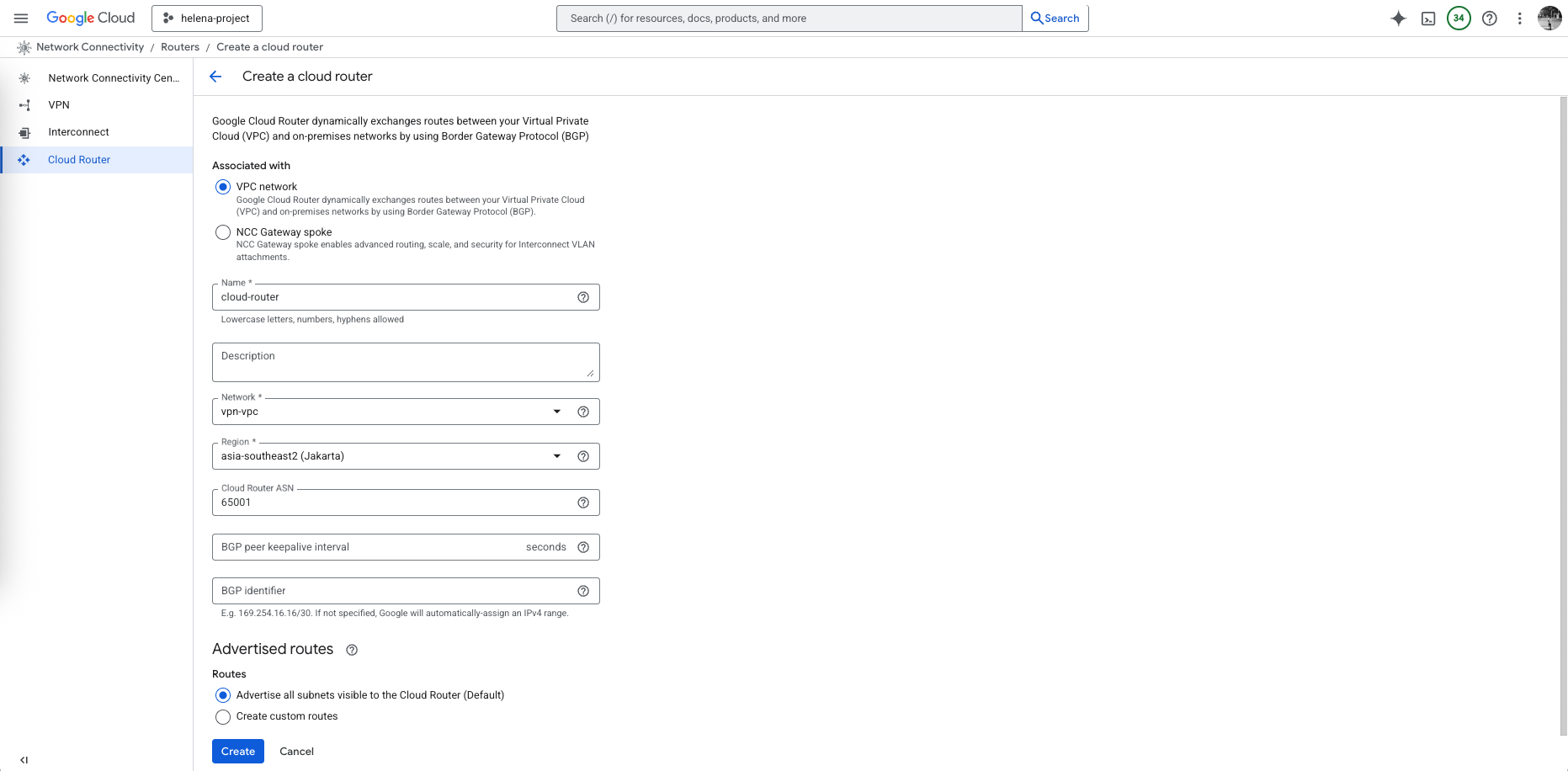
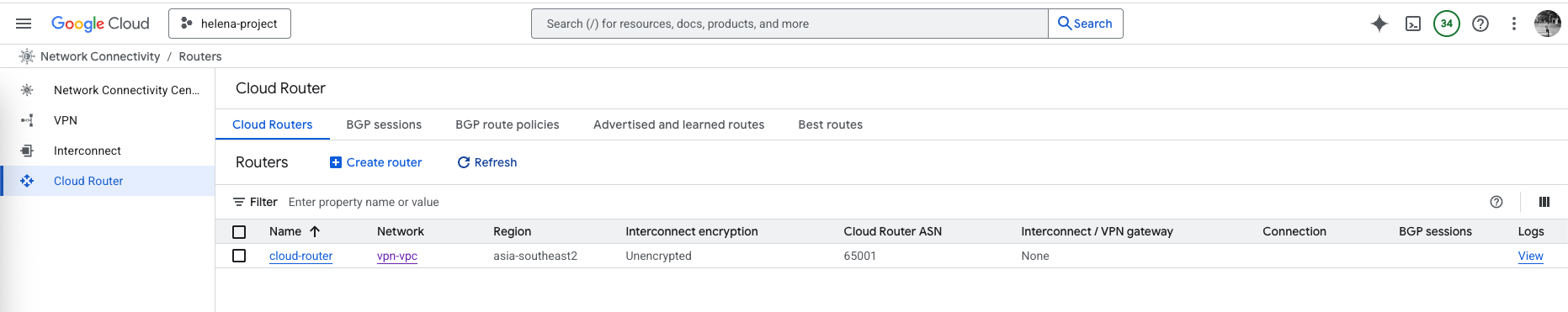
Configuring Cloud Router
Next we set up a Cloud Router as our virtual router on GCP, here we attach it to our VPC and give a BGP AS Number of 65001, and configure it to advertise all known networks
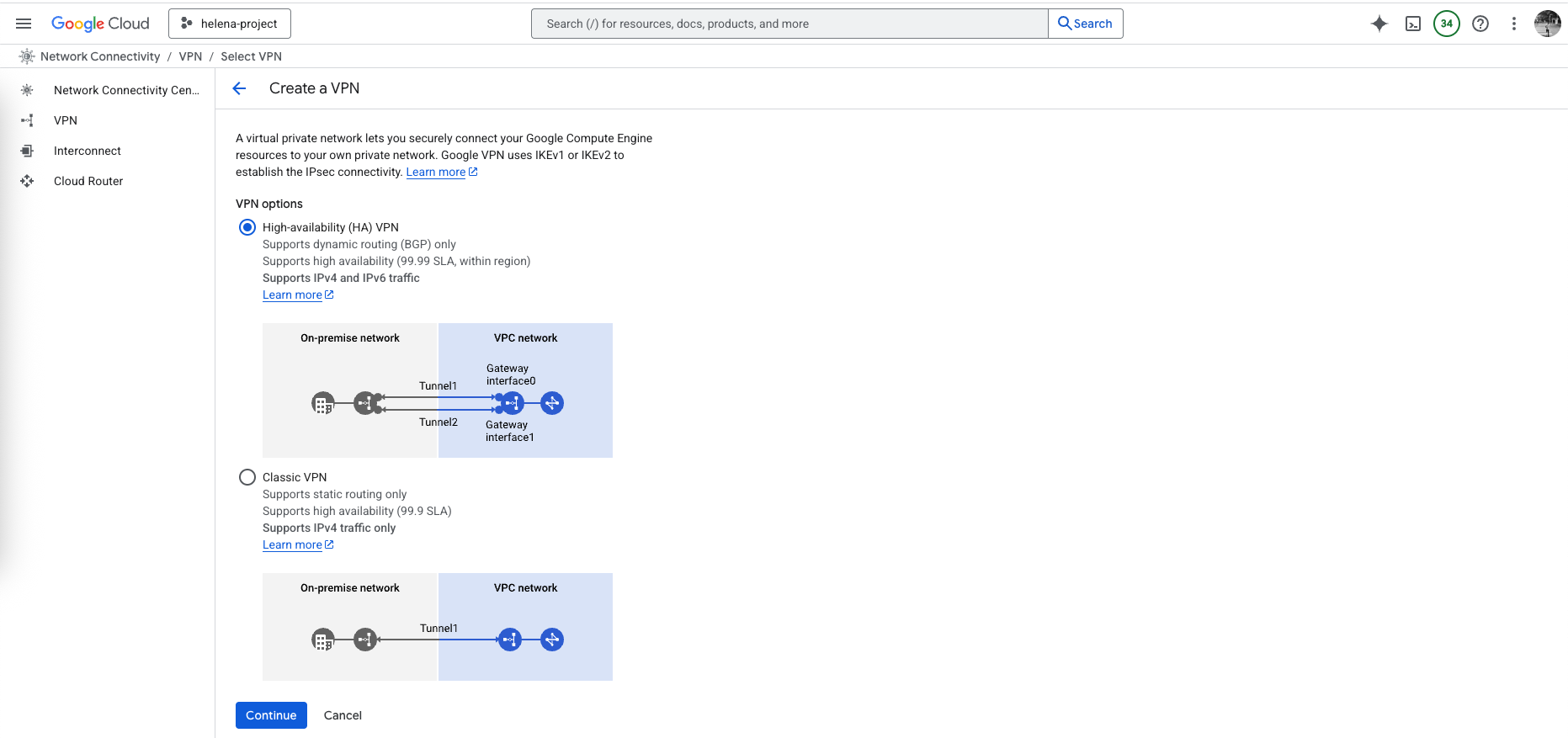
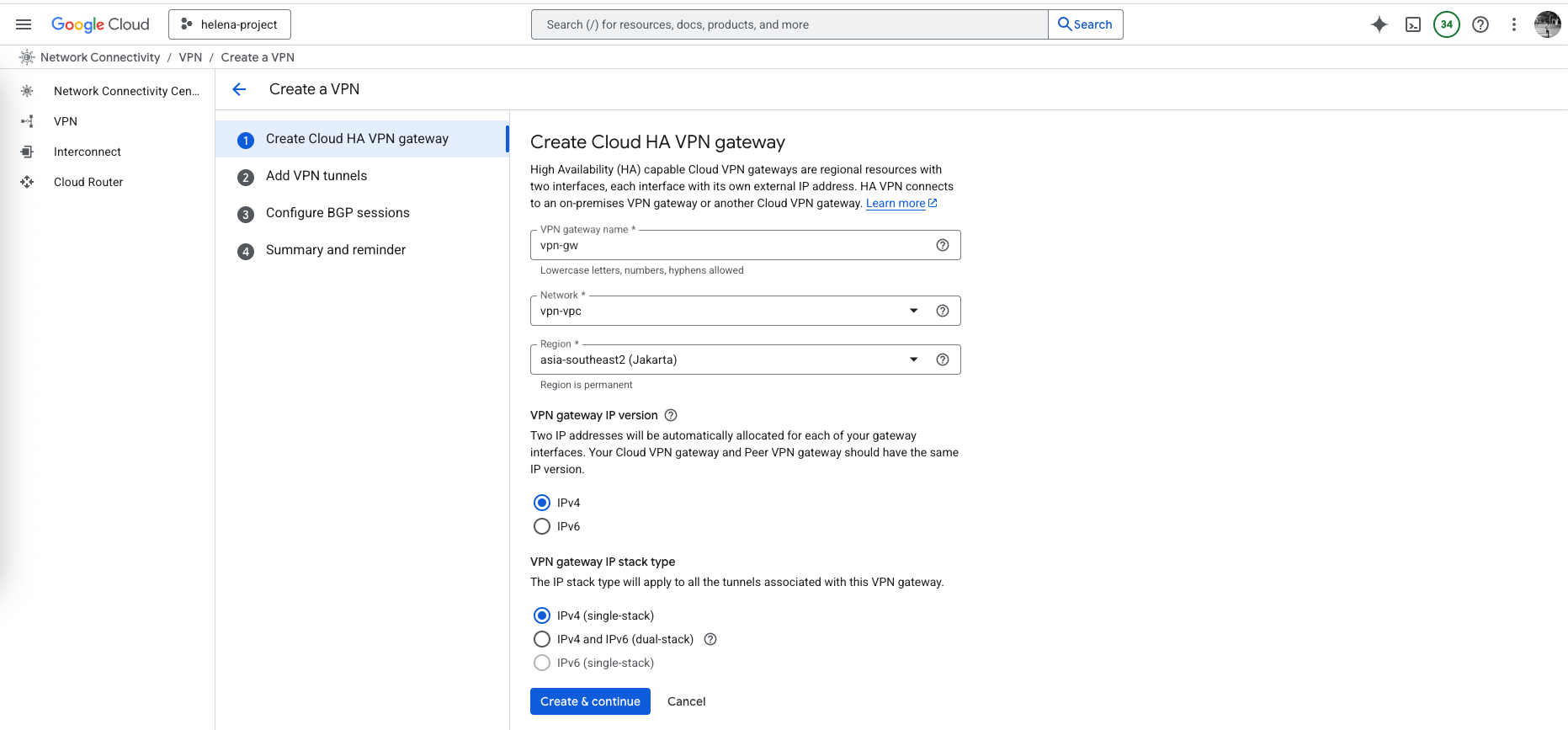
Configuring HA VPN
Next we configure the HA VPN
Here we give it name and associate it with our VPC.
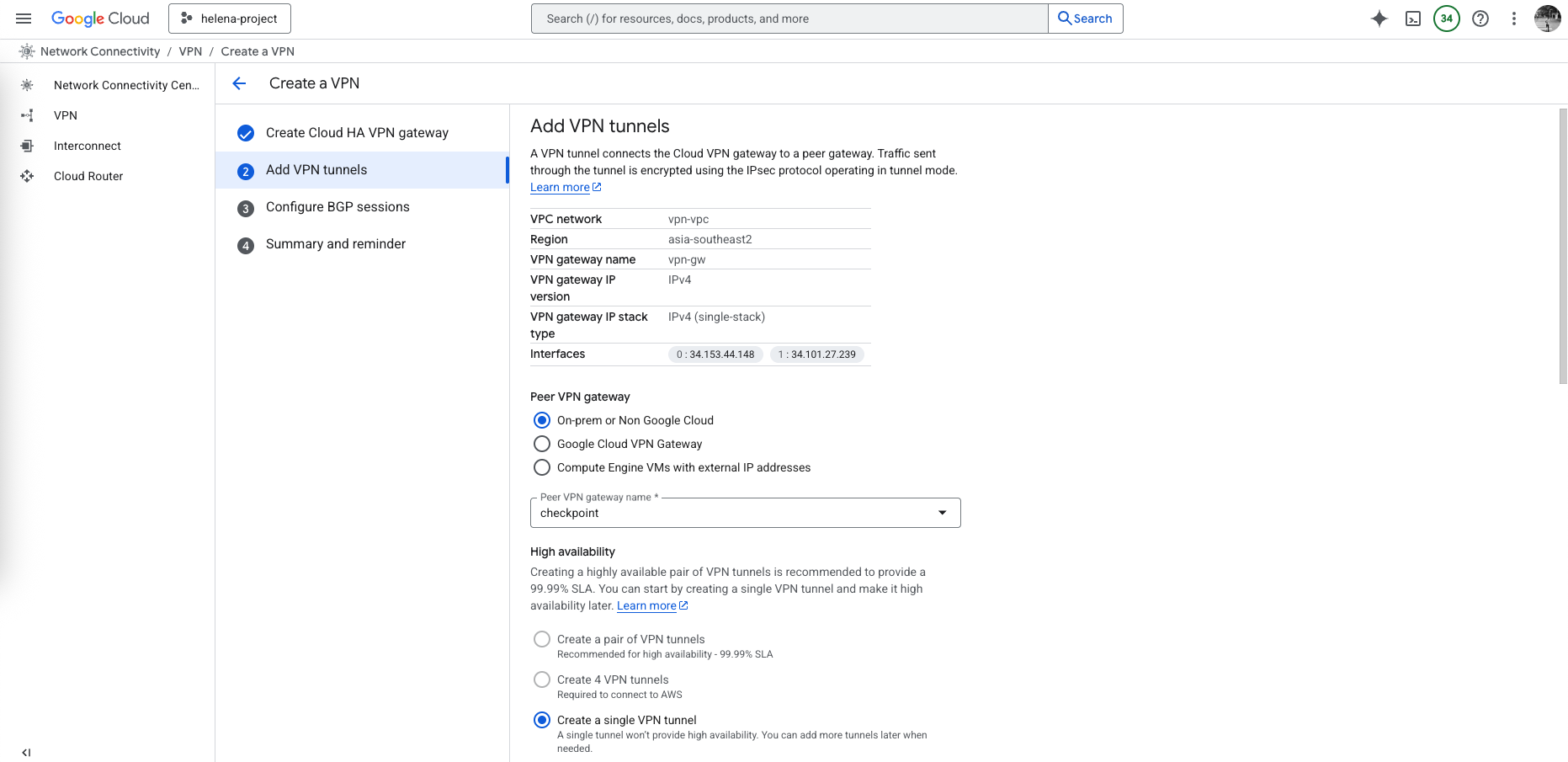
On here we setup tunnel to our On-premise Check Point firewall
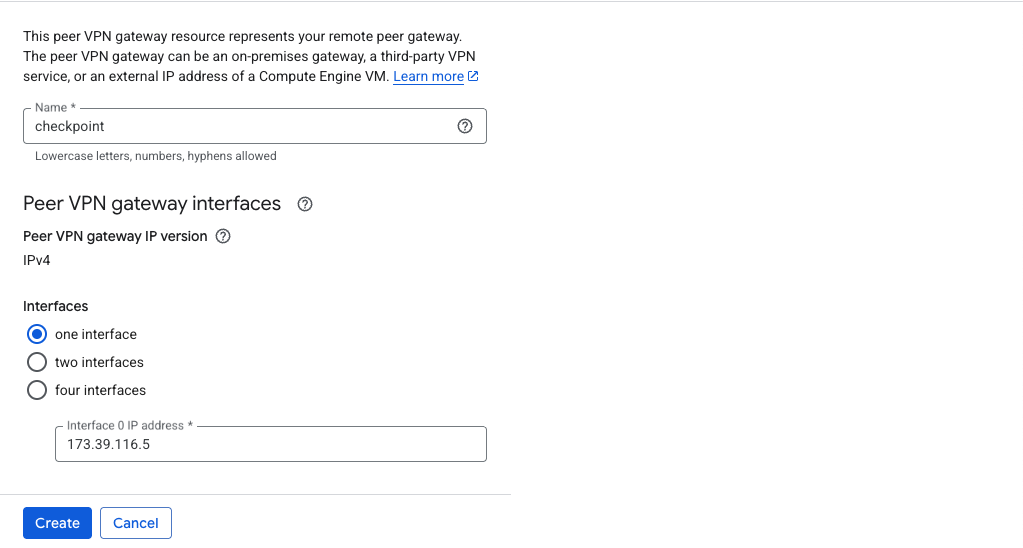
The peer check point object contains the public IP Address of the firewall, keep in mind this device is sitting behind NAT and is not directly accessible by the public IP
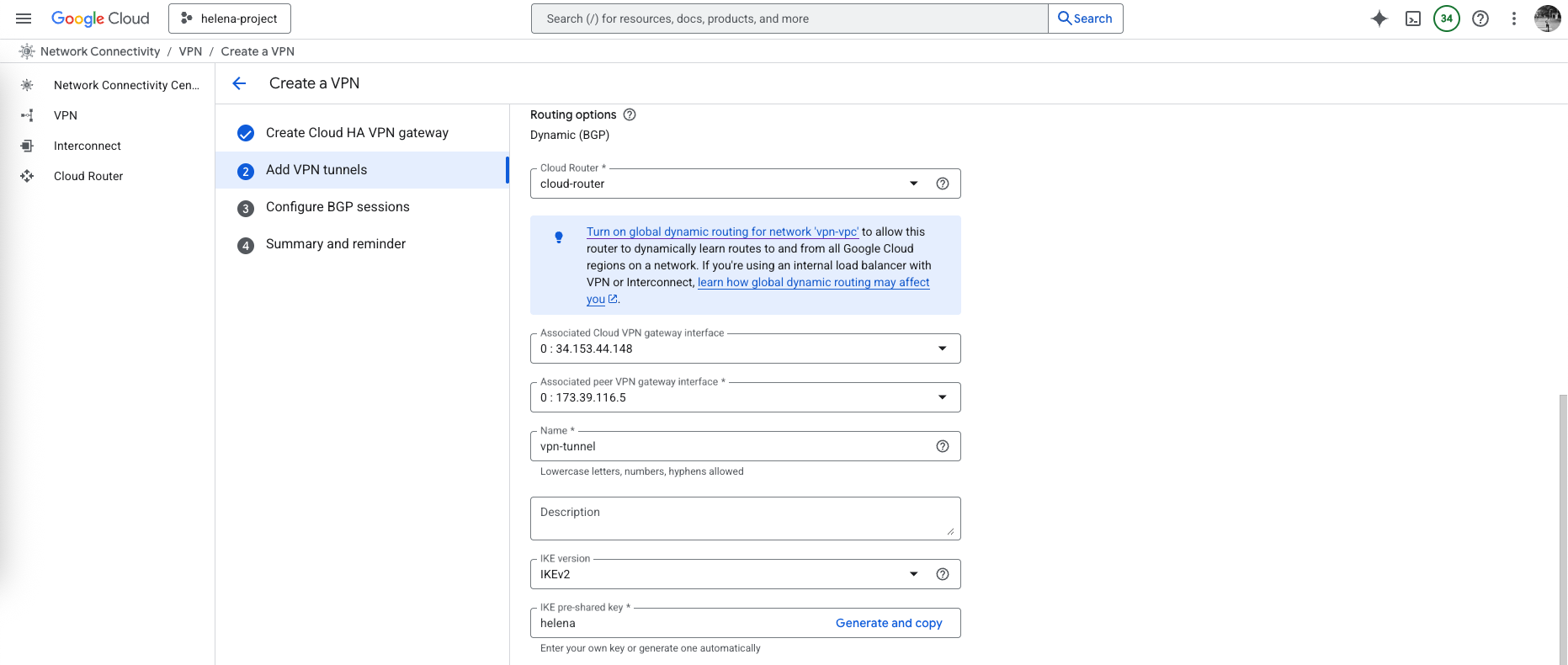
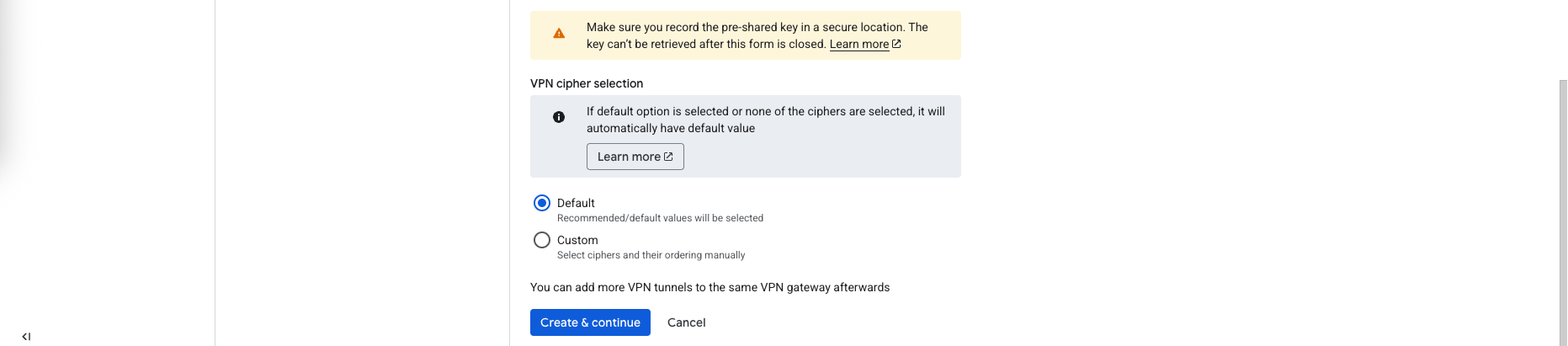
Scroll down to the routing options we select the Cloud Router and set up the Pre-shared Key
Then on cipher options, we’d just select the default option for simplicity
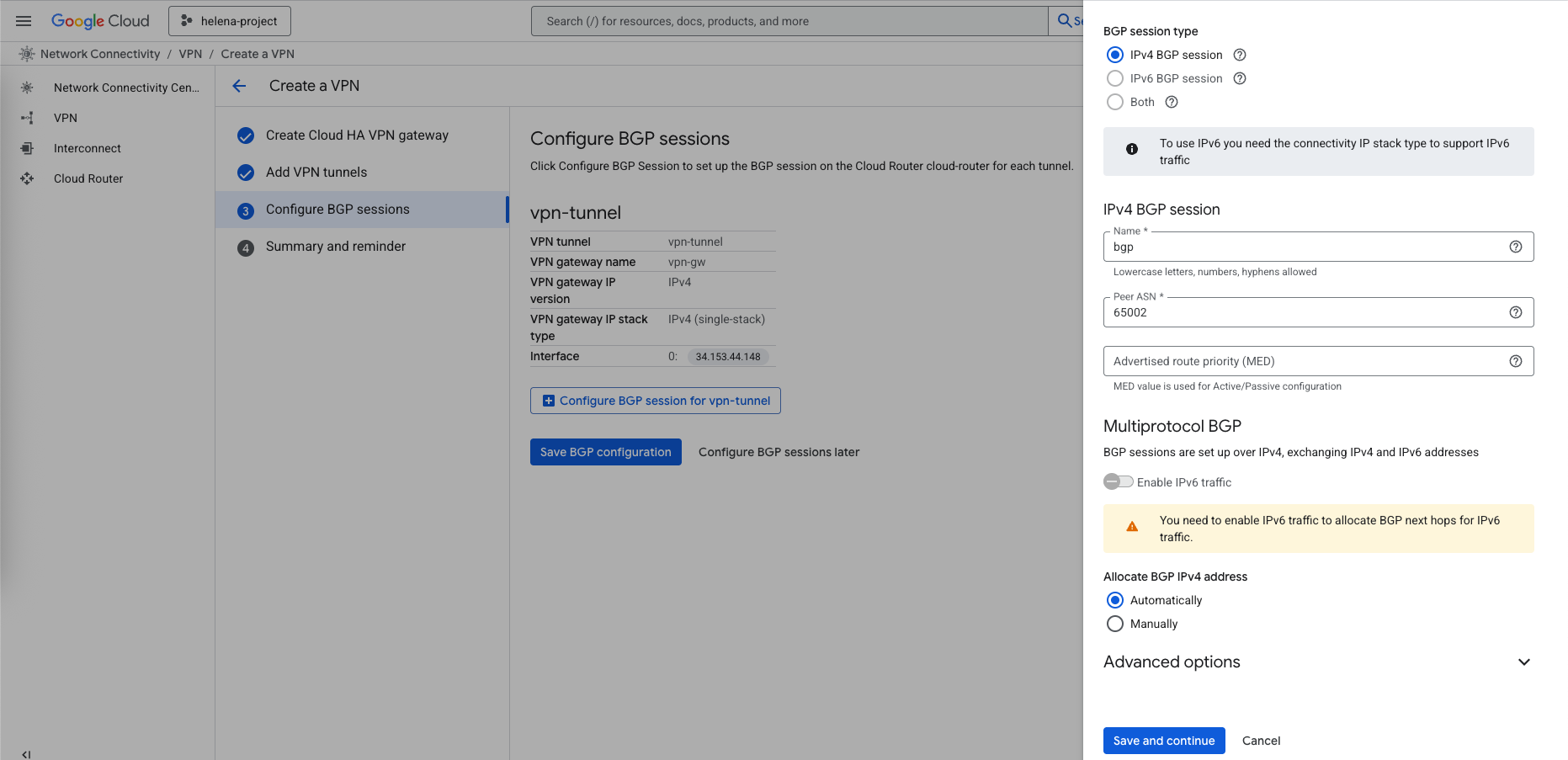
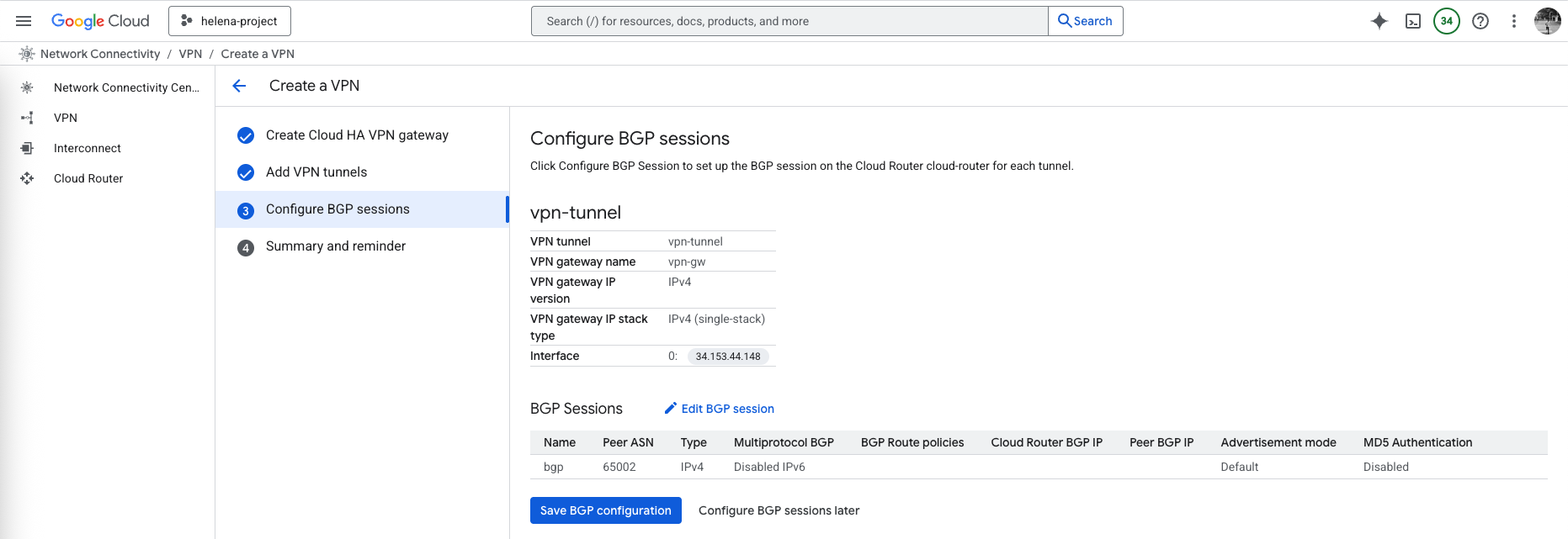
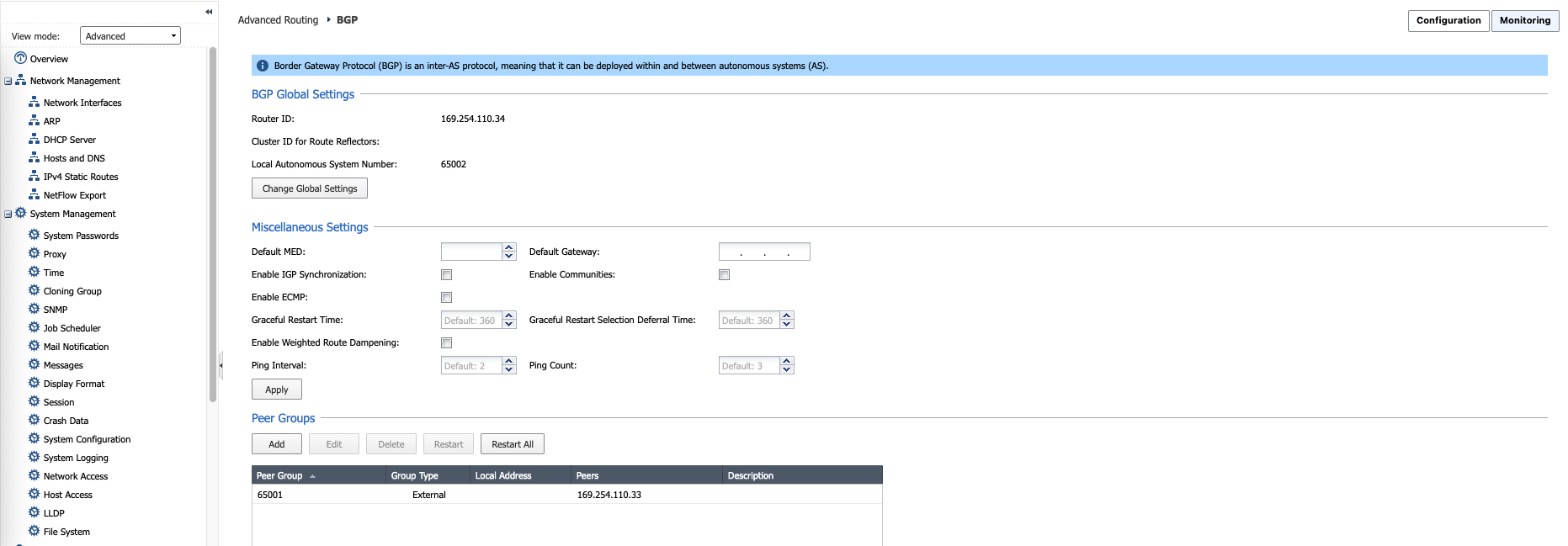
Next on BGP sessions, we configure the peer BGP on the On-prem CP that uses AS Number 65002
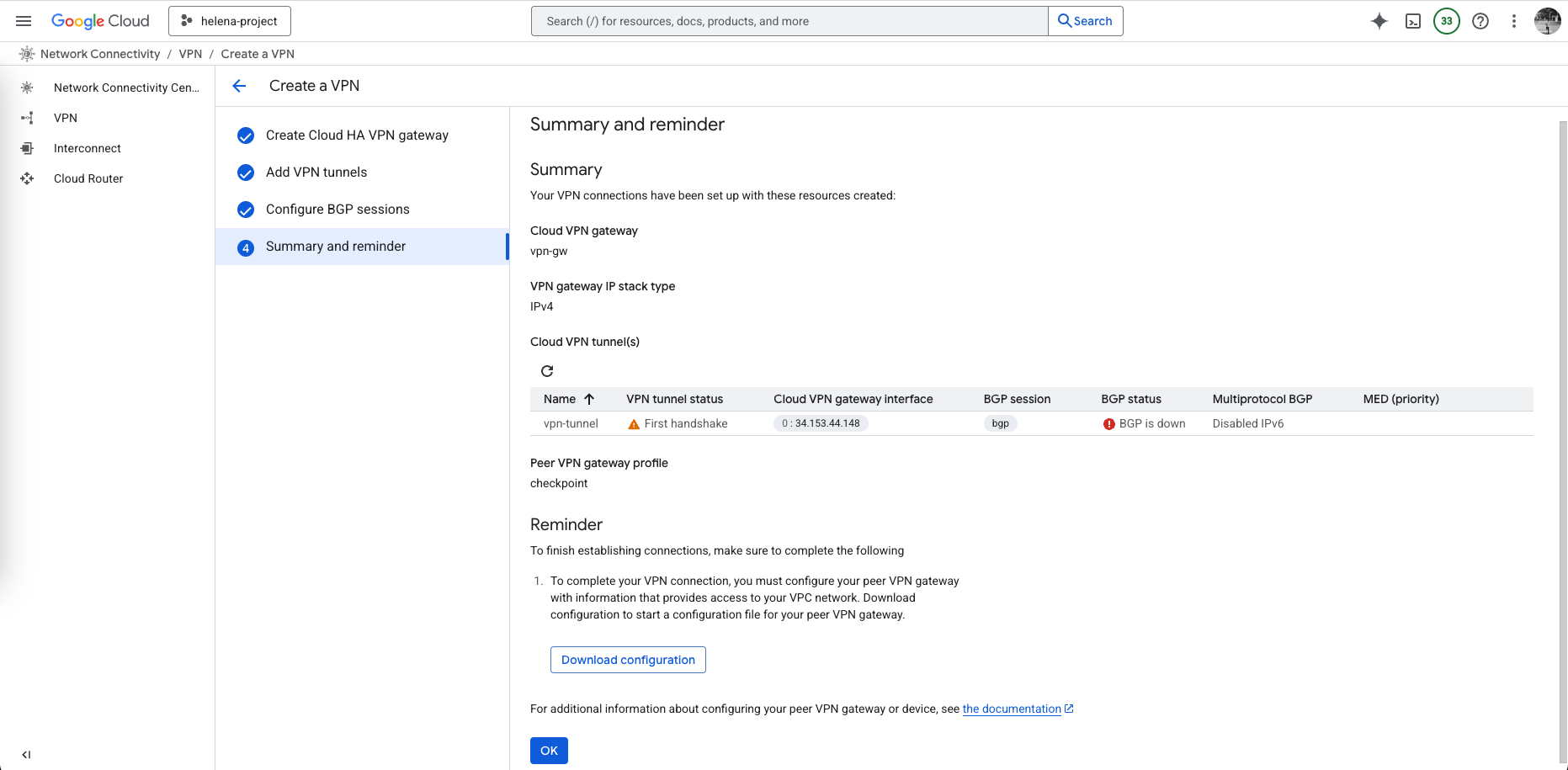
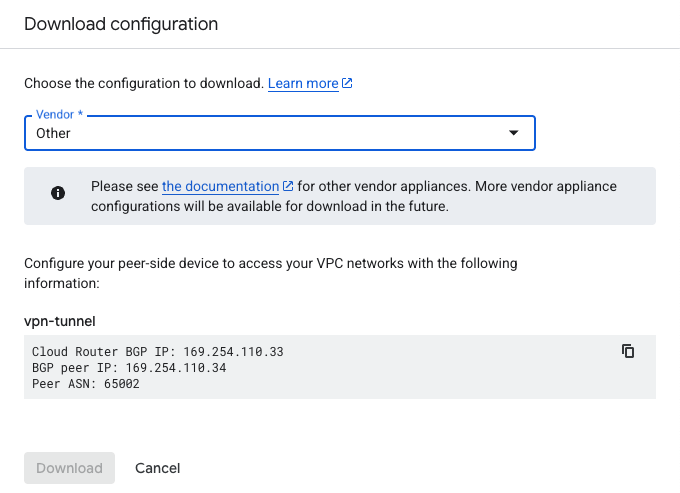
And finally on the summary page, we can download our configuration to be used to configure on the on-prem side
This VPN Wizard automatically creates these 3 configurations
Configuring Check Point VPN
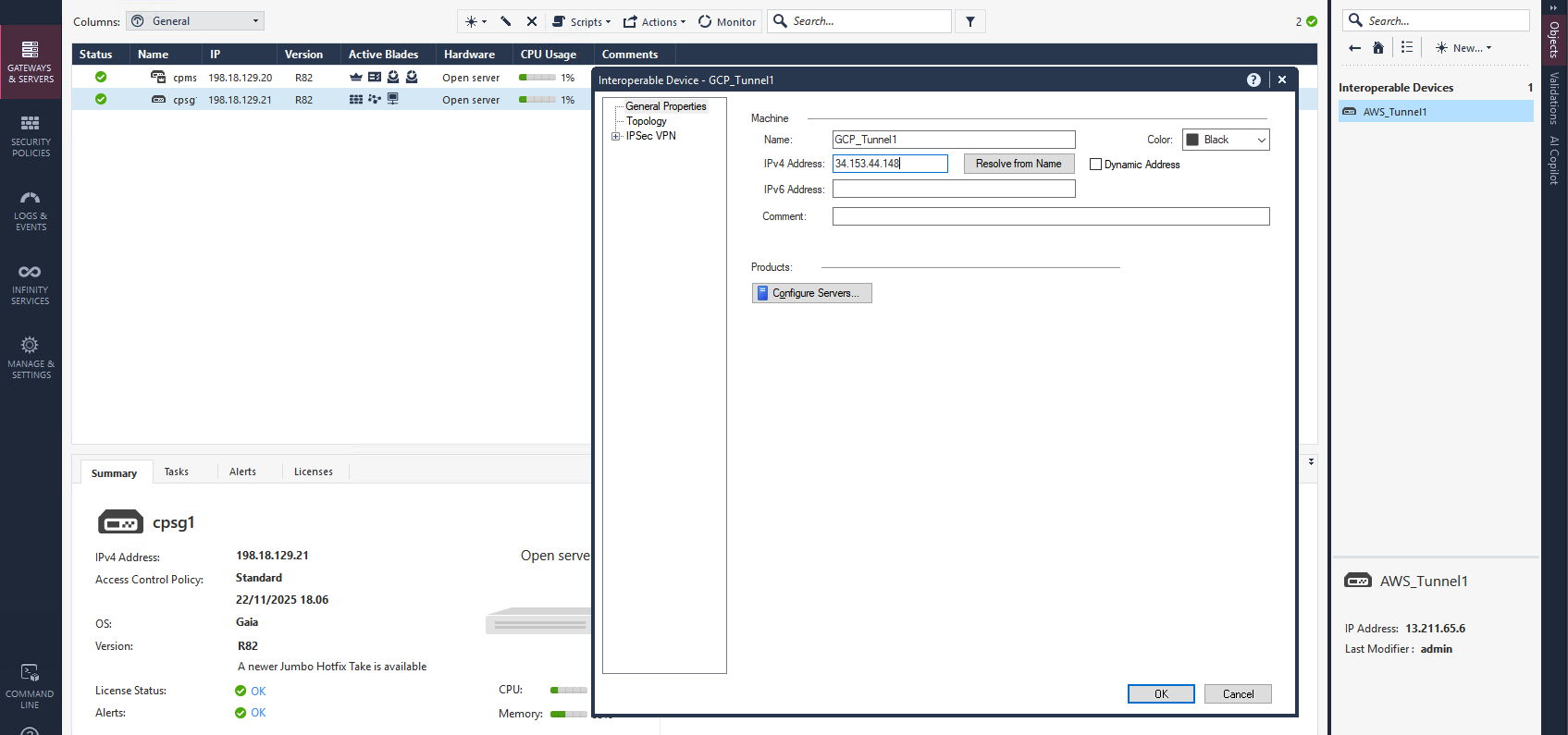
On Check Point side, we create a new Interoperable Device named GCP_Tunnel1 with GCP’s public IP Address
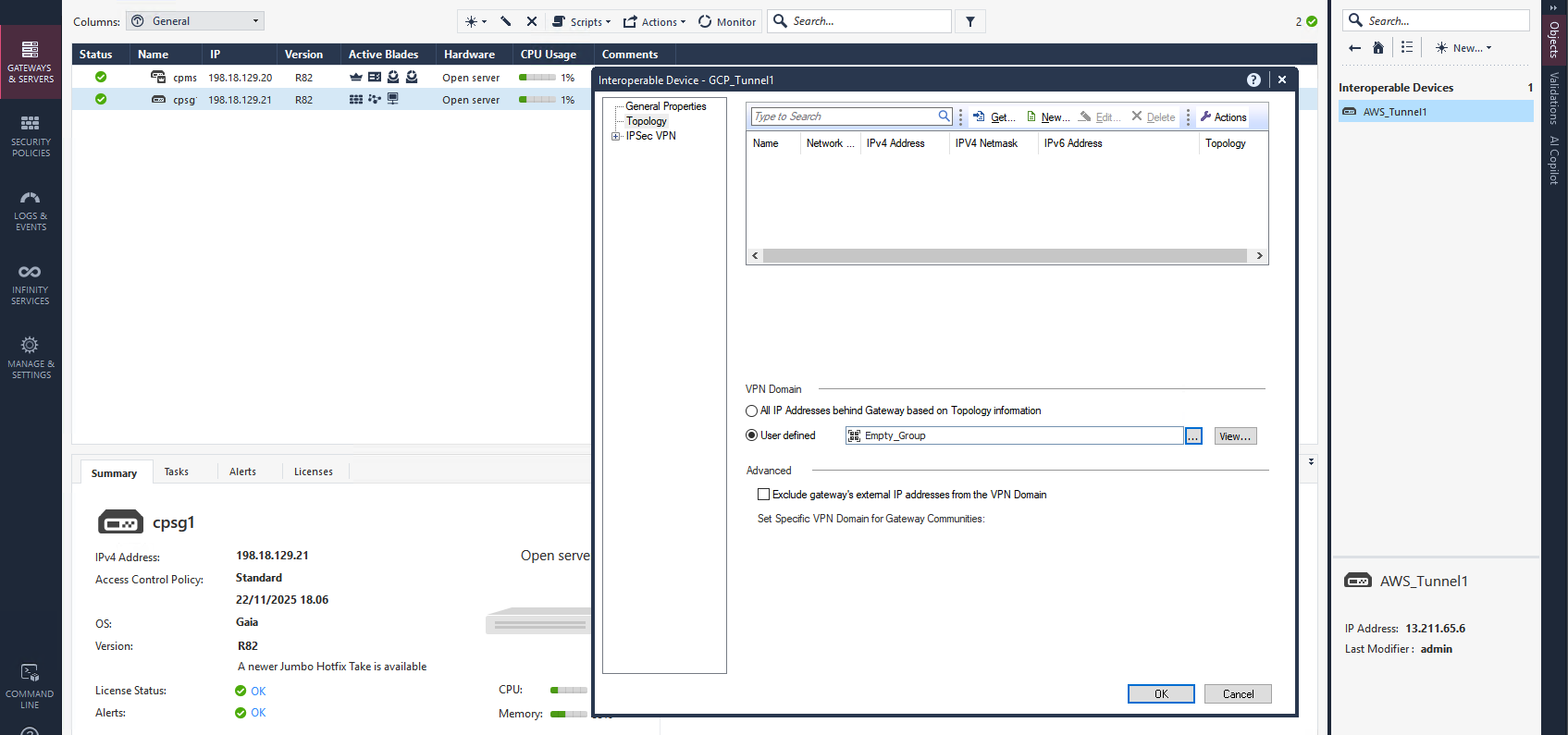
On Topology, we make sure to use Empty Group on the VPN Domain so the VPN will use routing table to decide which traffic will be encrypted
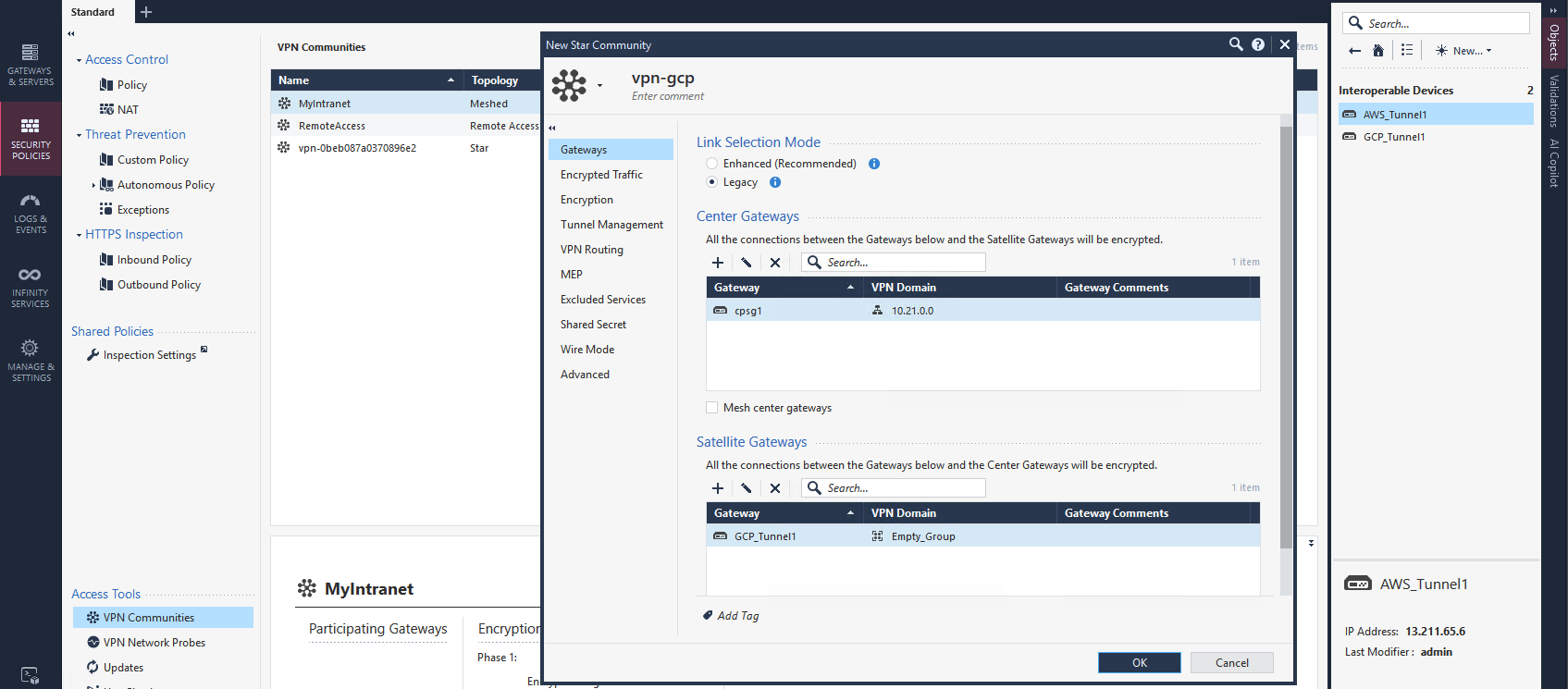
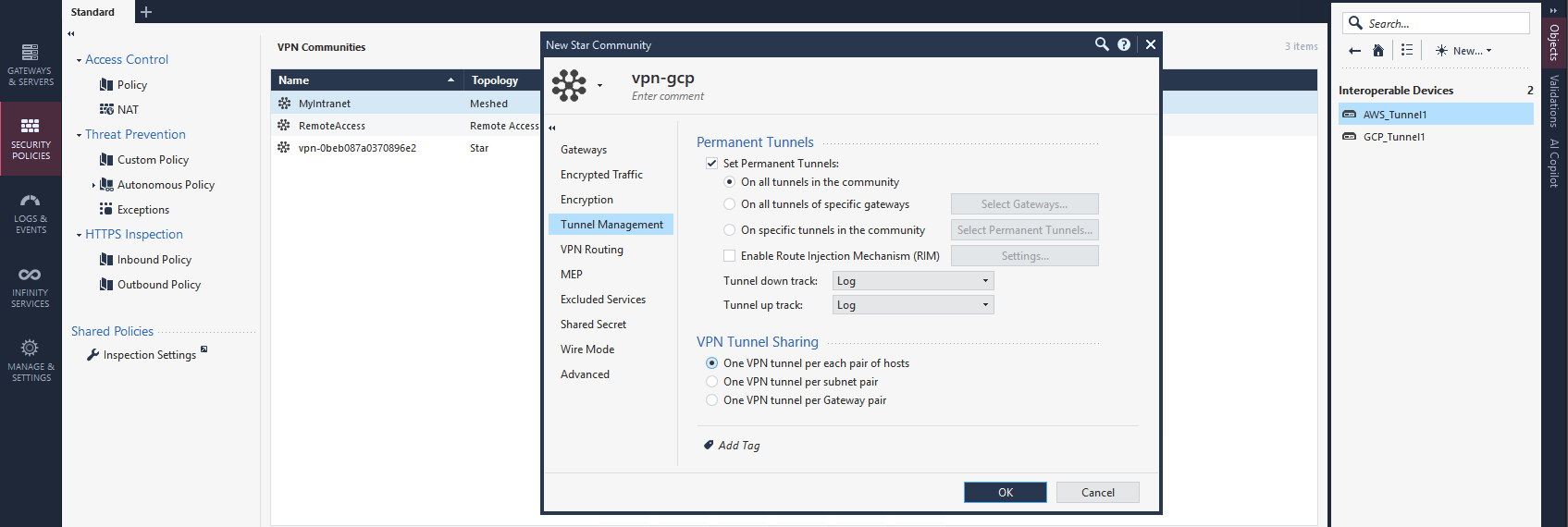
Next we create a Star Community selecting our CP as Center Gateways and GCP as Satellite Gateways
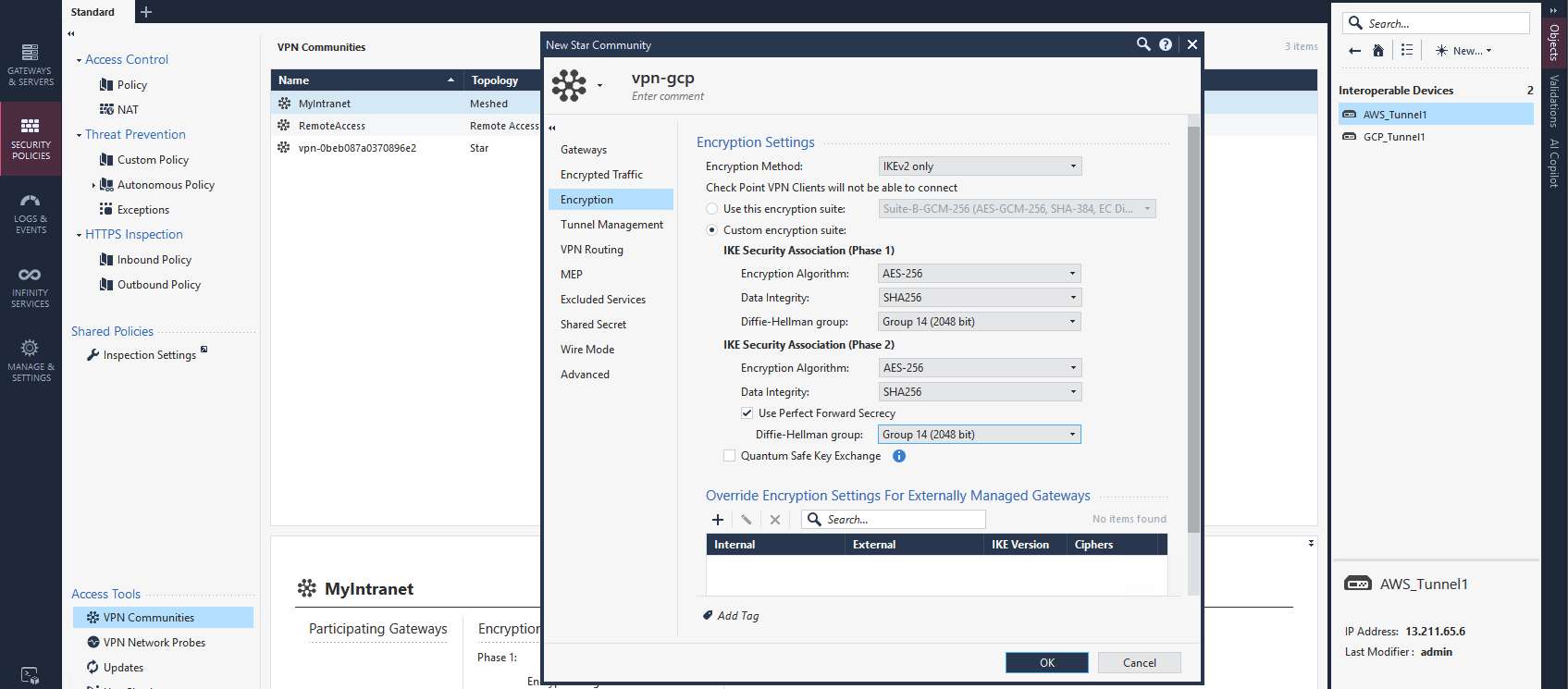
Then we configure the ciphers following the supported setup by GCP
Next we enable Permanent Tunnels
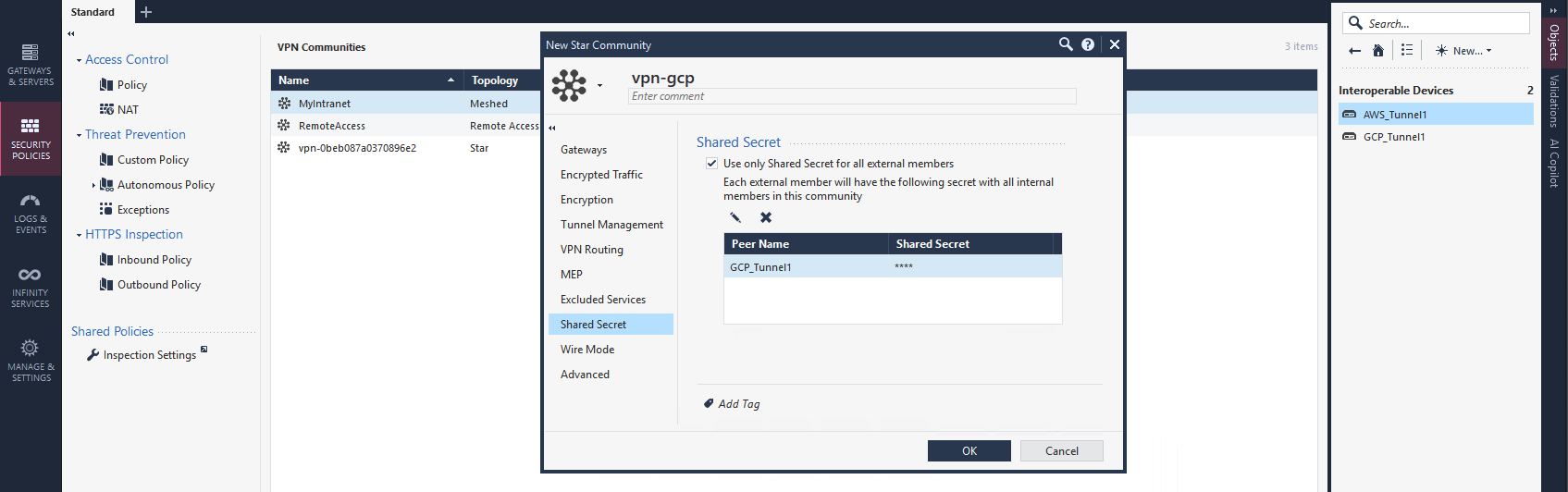
And finally we configure the Pre-share Key
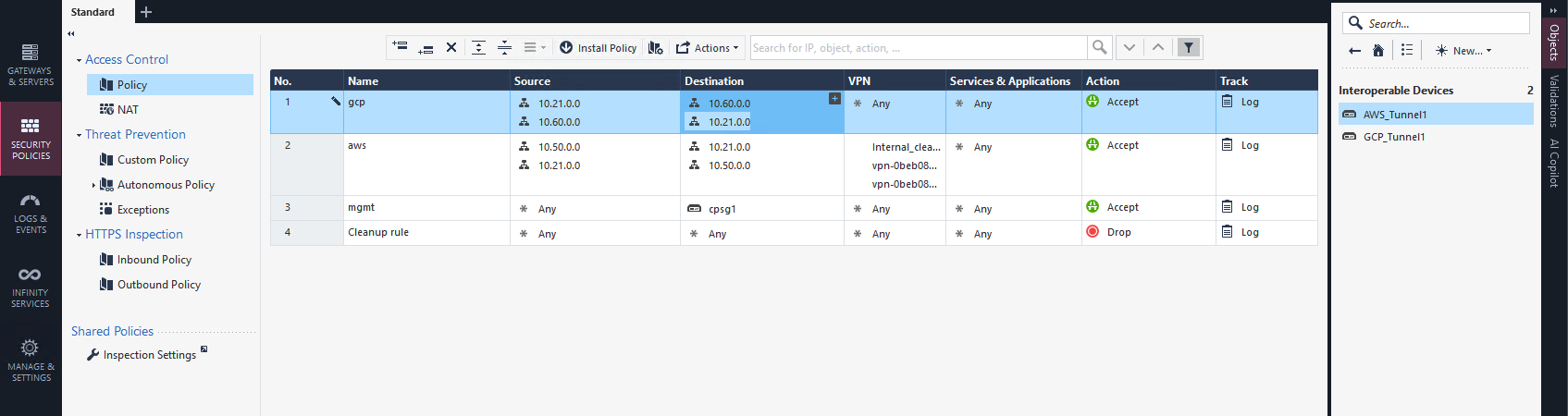
And we also add a rule policy to allow traffic going between the 2 subnets
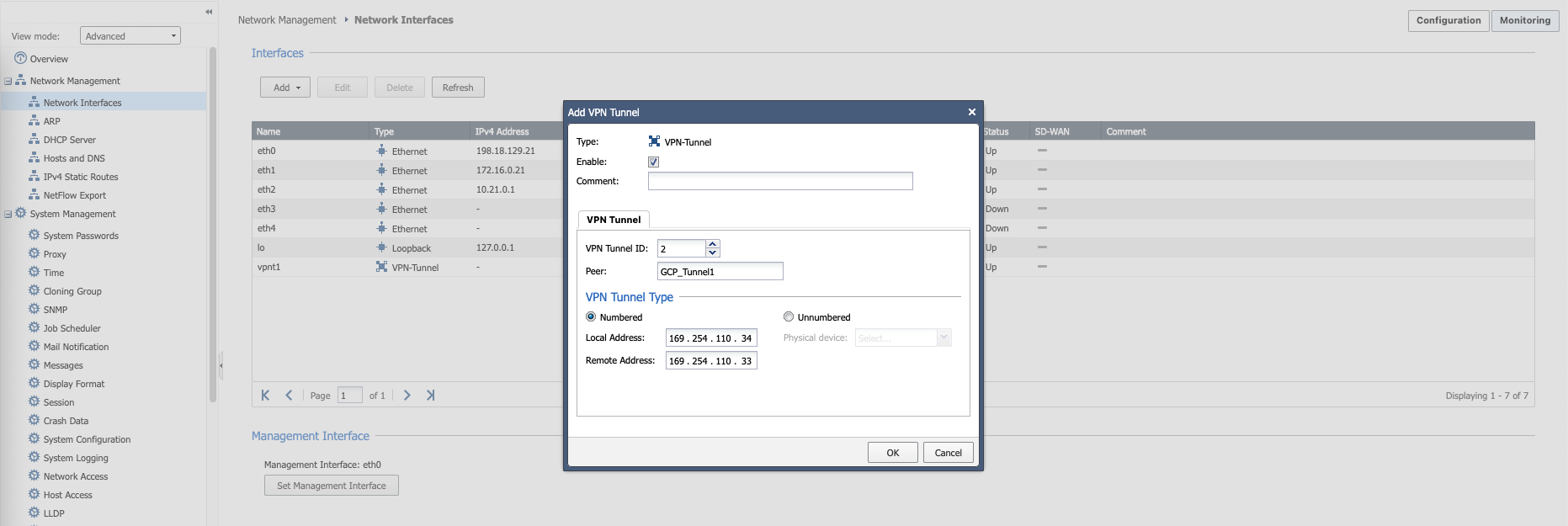
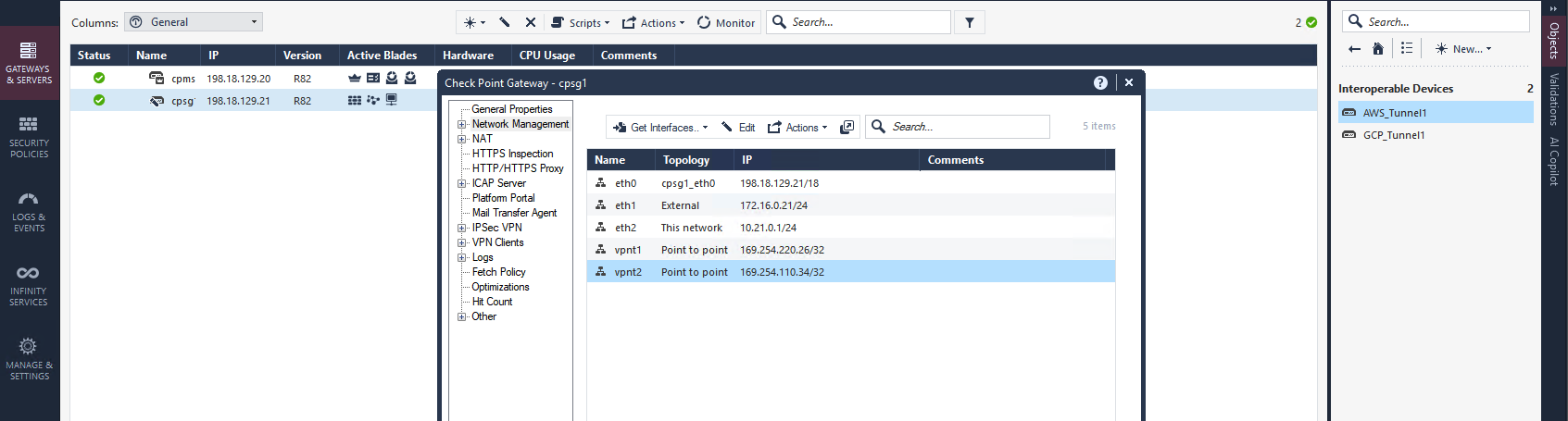
After that, we create a Tunnel Interface with peer name following the Interoperable Device name and IP Addressing following the downloaded configuration from GCP
And we enable BGP to receive and advertise routes between GCP and On-premise
Lastly we import the interface so it shows up on Smart Console, and that should wrap up the configurations
Verifying VPN
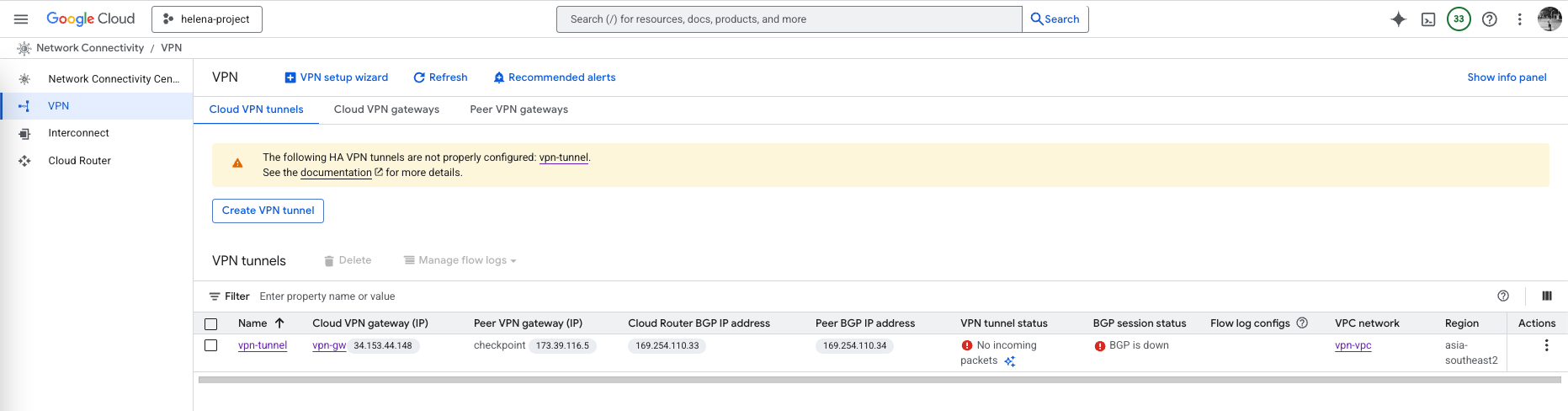
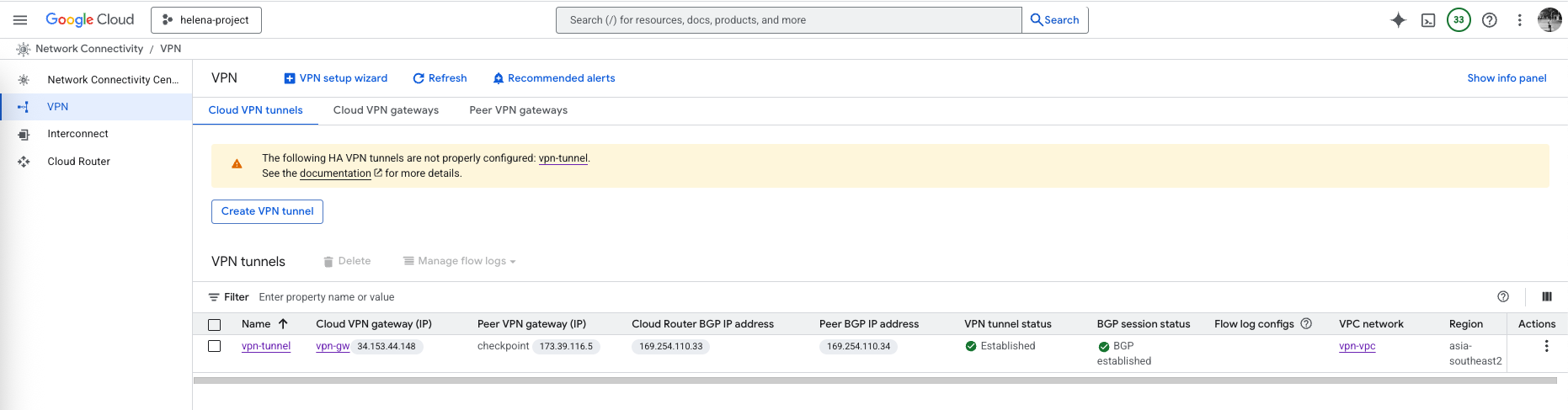
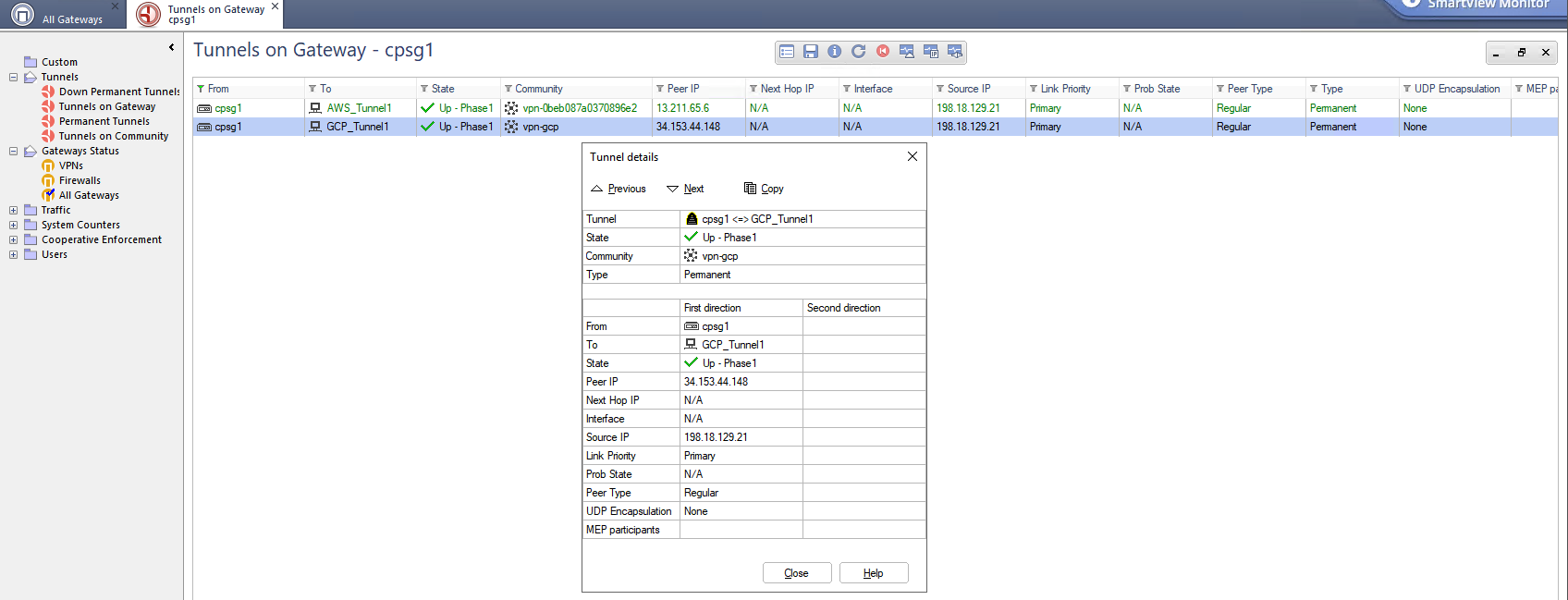
On GCP side, we can see both Tunnel and BGP sessions are established
Same goes if we verify it on the Check Point side
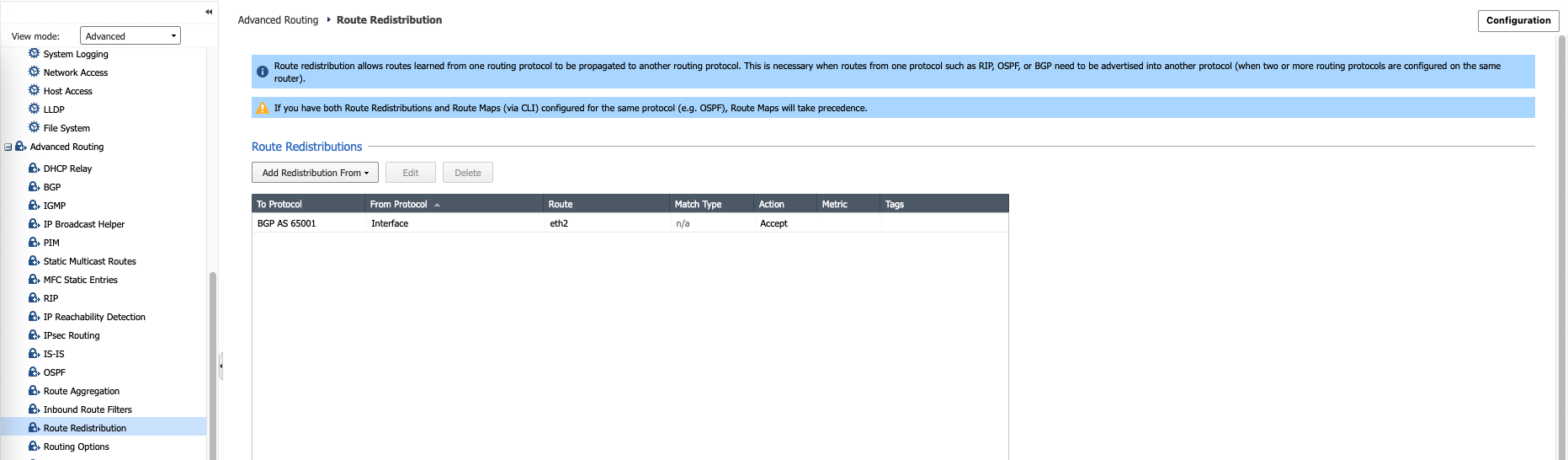
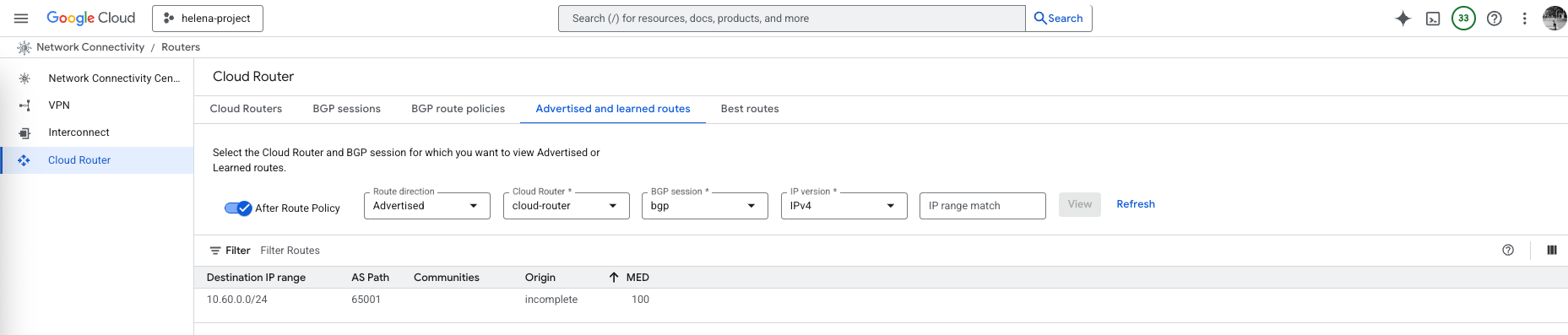
On GCP’s Cloud Router, we verify that it’s advertising the 10.60.0.0/24 to BGP
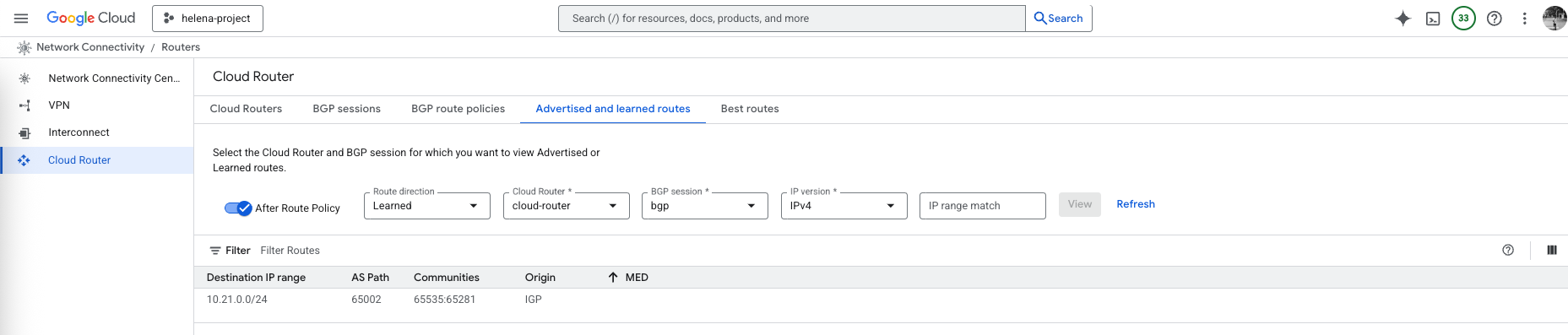
And it’s also receiving 10.21.0.0/24 from BGP
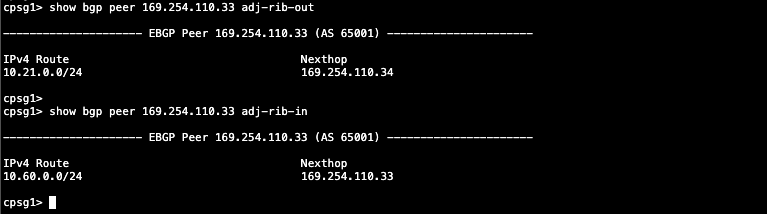
Same goes with CP, the BGP session has successfully received 10.60.0.0/24 from GCP and advertise 10.21.0.0/24 to GCP
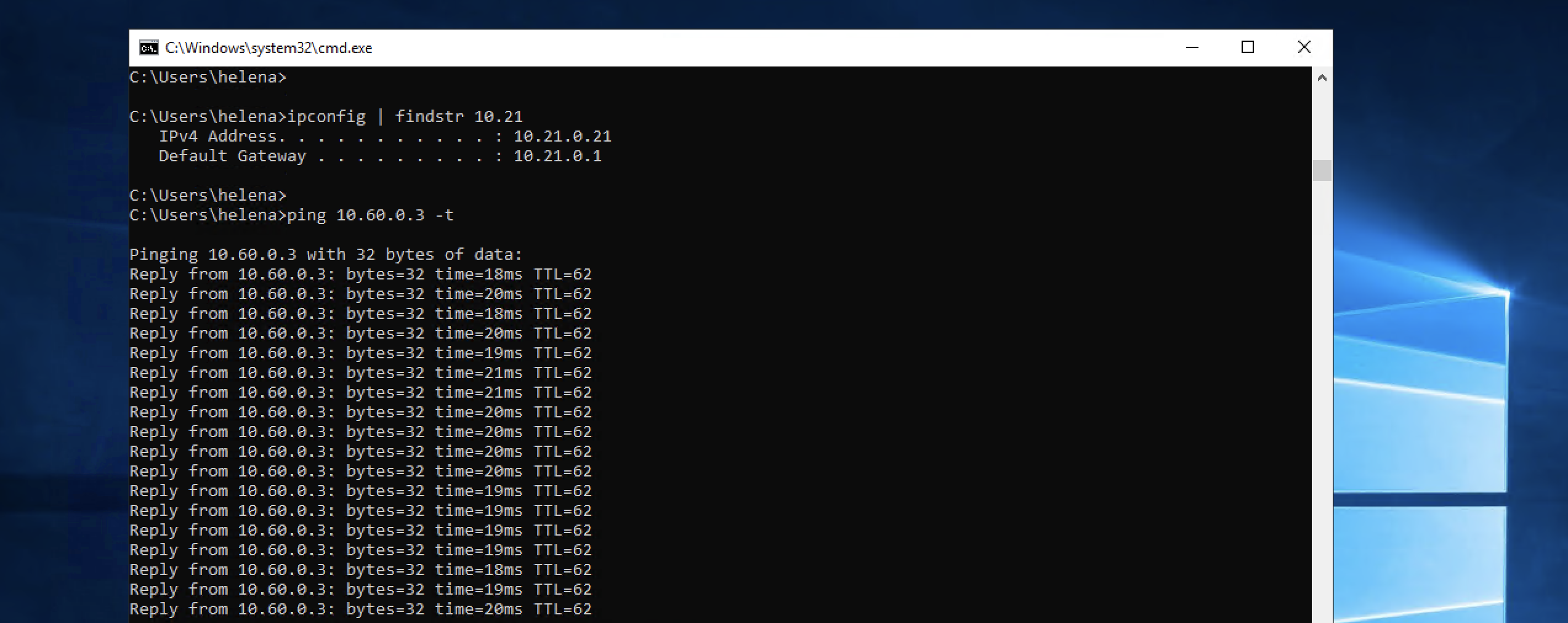
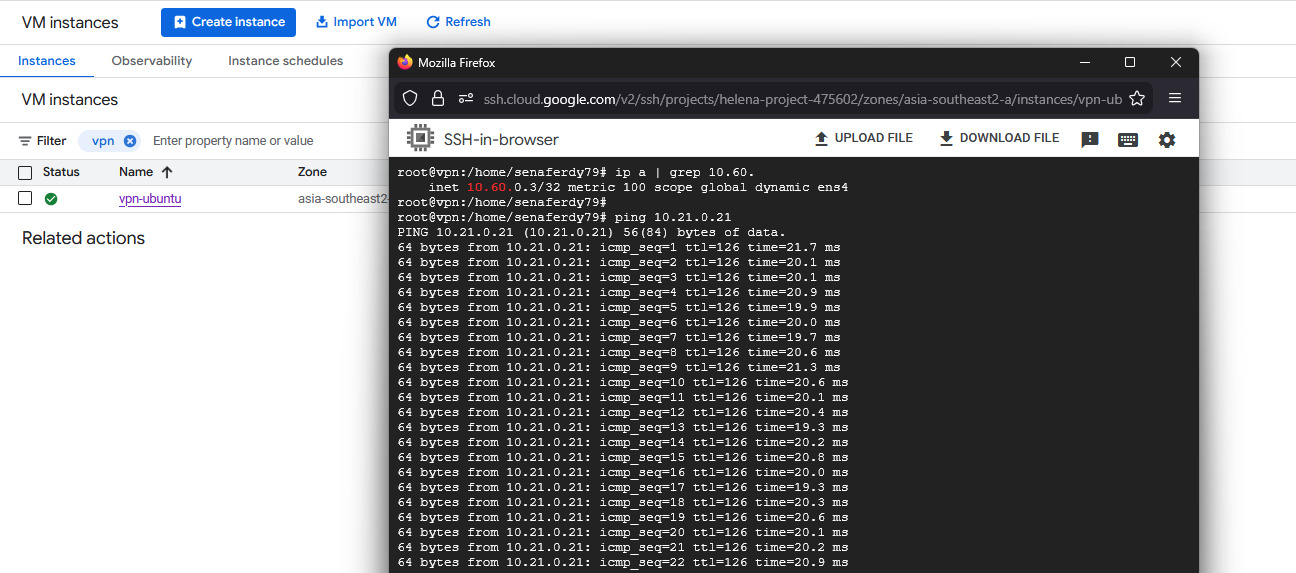
And we’re also able to connect between the two hosts on GCP and On-prem
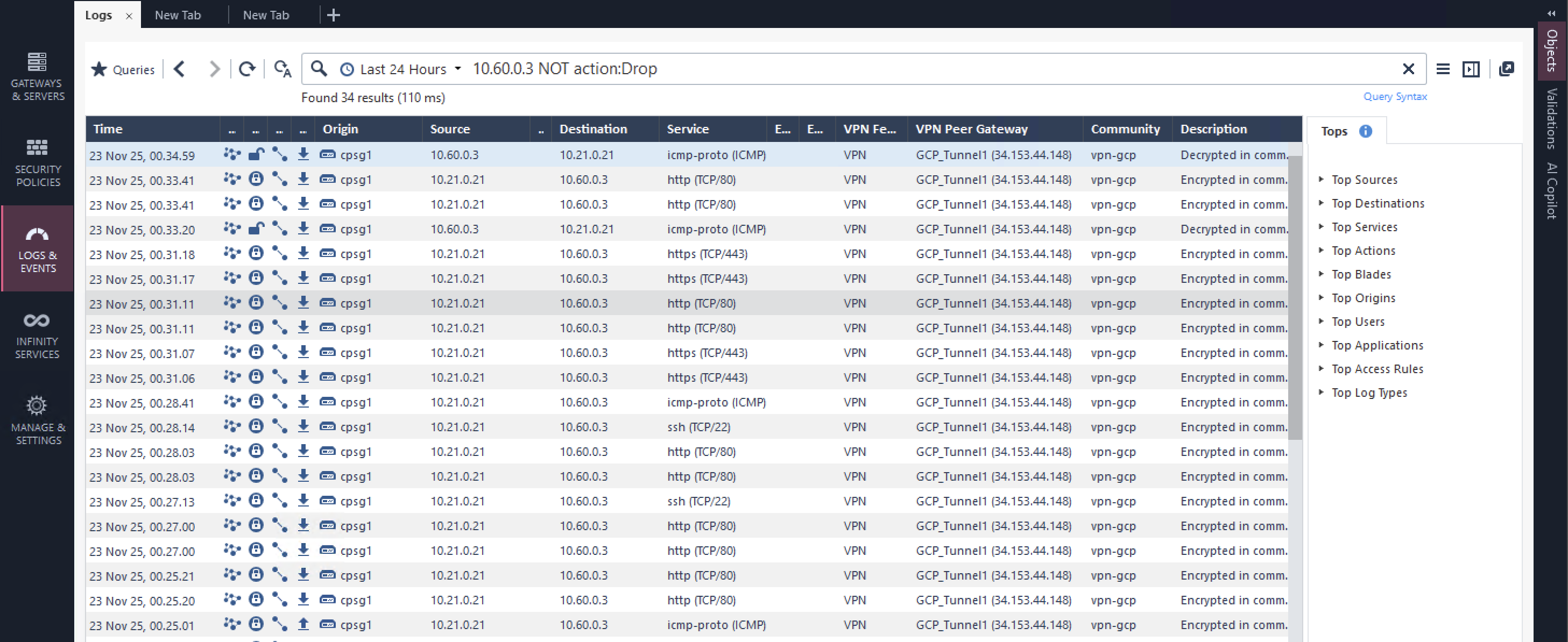
With logs showing up on CP verifying VPN and BGP connections are working perfectly